Hello Folks, Welcome back to the second part of our journey to transition from the Log Analytics agents to the Azure Monitor Agent (AMA). In the first part, we learned how to find and check the monitoring agents using KQL. In this part, we'll continue our journey by identifying the agents that have reported to the Log Analytics Workspace and then extend our query to include all virtual machines within your subscription or tenant.
Last time, we discovered which virtual machines were running the old MMA or OMS agents. This time, we're refining our search to quickly determine whether a machine uses MMA or the updated AMA.
📊 Extending the query to include extensions for AMA
If you recollect from our previous post, we explored the microsoft.compute/virtualmachines/extensions table in the Azure Resource Graph to look up the virtual machines and their extensions. We picked out just the extensions we needed. Now, we're taking it a step further. We want to see the extensions on the virtual machines, especially the ones for the AMA agent.
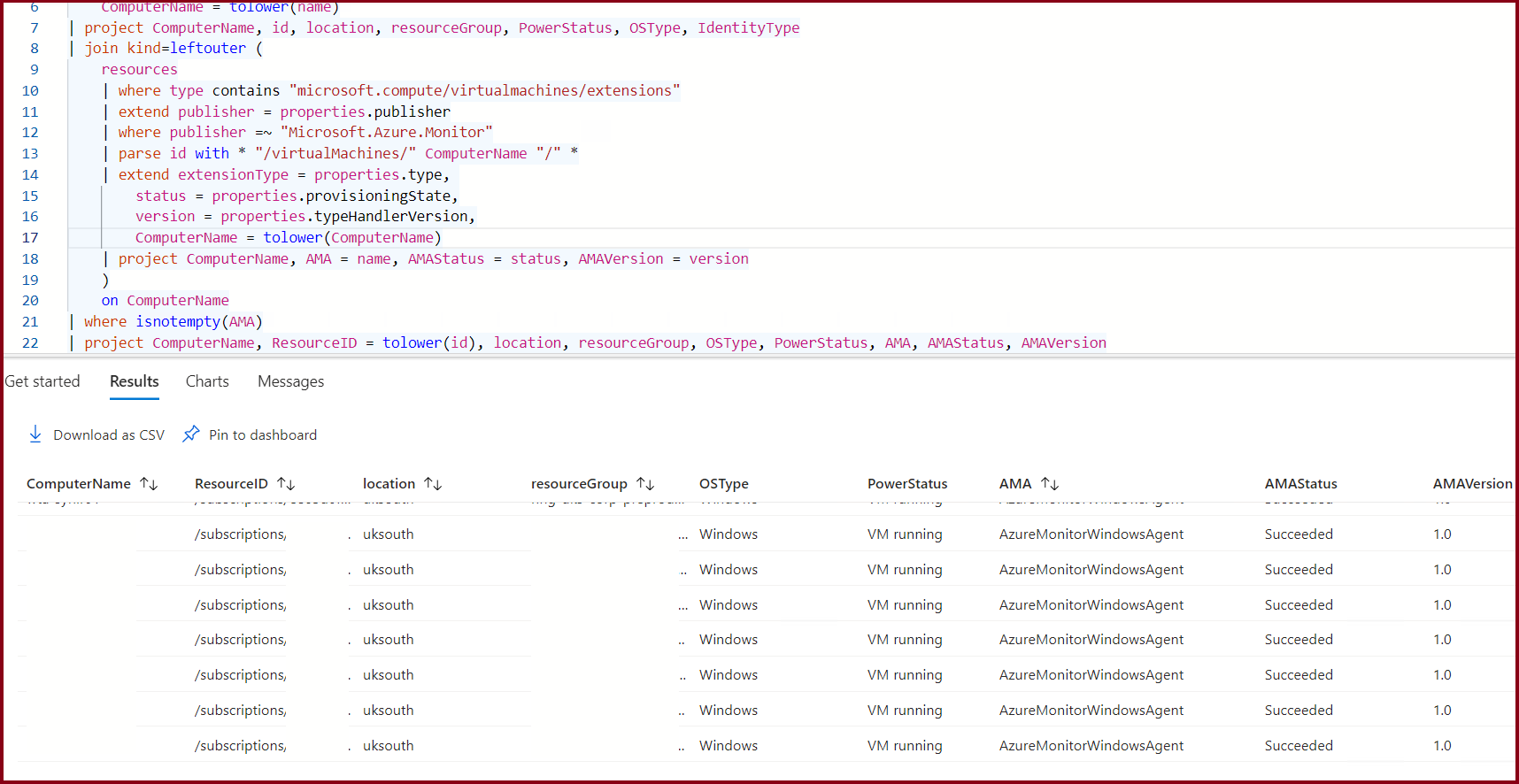
In order to do this, we are going to use the filter publisher =~ "Microsoft.Azure.Monitor for the AMA agent. Here's how we can extend our query to include the extensions for the AMA agent:
resources
| where type == "microsoft.compute/virtualmachines"
| extend PowerStatus = properties.extended.instanceView.powerState.displayStatus,
OSType = properties.storageProfile.osDisk.osType,
IdentityType = identity.type,
ComputerName = tolower(name)
| project ComputerName, id, location, resourceGroup, PowerStatus, OSType, IdentityType
| join kind=leftouter (
resources
| where type contains "microsoft.compute/virtualmachines/extensions"
| extend publisher = properties.publisher
| where publisher =~ "Microsoft.Azure.Monitor"
| parse id with * "/virtualMachines/" ComputerName "/" *
| extend extensionType = properties.type,
status = properties.provisioningState,
version = properties.typeHandlerVersion,
ComputerName = tolower(ComputerName)
| project ComputerName, AMA = name, AMAStatus = status, AMAVersion = version
)
on ComputerName
| where isnotempty(AMA)
| project ComputerName, ResourceID = tolower(id), location, resourceGroup, OSType, PowerStatus, AMA, AMAStatus, AMAVersion
Resulting in example output:
| COMPUTERNAME | LOCATION | RESOURCEGROUP | OSTYPE | POWERSTATUS | AMA | AMASTATUS | AMAVERSION |
|---|---|---|---|---|---|---|---|
| vm-name-01 | location-01 | rg-name-01 | Linux | VM deallocated | AzureMonitorLinuxAgent | Succeeded | 1 |
| vm-name-02 | location-02 | rg-name-02 | Linux | VM running | AzureMonitorLinuxAgent | Succeeded | 1.22 |
| vm-name-03 | location-03 | rg-name-03 | Linux | VM running | AzureMonitorLinuxAgent | Succeeded | 1.6 |
| vm-name-04 | location-01 | rg-name-01 | Linux | VM running | AzureMonitorLinuxAgent | Succeeded | 1.6 |
▶️ Combine results for MMA and AMA
With the results for both MMA and AMA on the hand, we're in a strong position to bring them together for a holistic view of all our virtual machines and the respective agents reporting in. This comprehensive overview is crucial for grasping the current layout of our environment, which agents we need to transition.
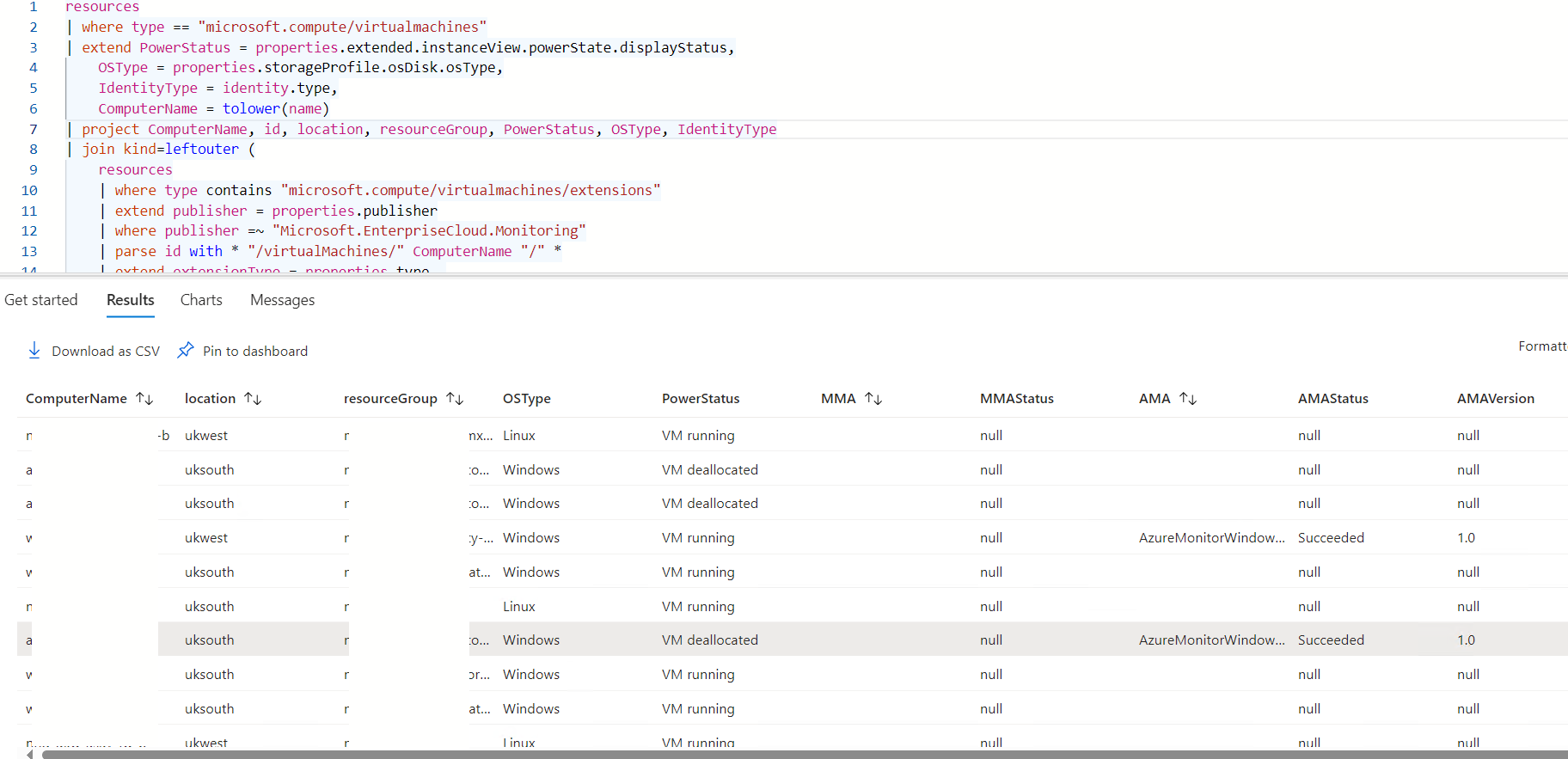
The process of generating these results into a single glass pane is straightforward. Merging these data sets isn't complex; we'll employ the same join keyword within our query to unify the information. By doing this, we'll gain a comprehensive overview of all the virtual machines and their respective reporting agents.
resources
| where type == "microsoft.compute/virtualmachines"
| extend PowerStatus = properties.extended.instanceView.powerState.displayStatus,
OSType = properties.storageProfile.osDisk.osType,
IdentityType = identity.type,
ComputerName = tolower(name)
| project ComputerName, id, location, resourceGroup, PowerStatus, OSType, IdentityType
| join kind=leftouter (
resources
| where type contains "microsoft.compute/virtualmachines/extensions"
| extend publisher = properties.publisher
| where publisher =~ "Microsoft.EnterpriseCloud.Monitoring"
| parse id with * "/virtualMachines/" ComputerName "/" *
| extend extensionType = properties.type,
status = properties.provisioningState,
version = properties.typeHandlerVersion,
ComputerName = tolower(ComputerName)
| project ComputerName, MMA = name, MMAStatus = status, version
)
on ComputerName
| join kind=leftouter (
resources
| where type contains "microsoft.compute/virtualmachines/extensions"
| extend publisher = properties.publisher
| where publisher =~ "Microsoft.Azure.Monitor"
| parse id with * "/virtualMachines/" ComputerName "/" *
| extend extensionType = properties.type,
status = properties.provisioningState,
version = properties.typeHandlerVersion,
ComputerName = tolower(ComputerName)
| project ComputerName, AMA = name, AMAStatus = status, AMAVersion = version
)
on ComputerName
| project ComputerName, location, resourceGroup, OSType, PowerStatus, MMA, MMAStatus, AMA, AMAStatus, AMAVersion
Below you'll find the results to help understand what we're looking at. Notice that in some cases, organizations are still running MMA, while others have already made the jump to AMA. This means we're seeing both agents in our environment, which could result in double logging from the same virtual machines.
| COMPUTERNAME | LOCATION | RESOURCEGROUP | OSTYPE | POWERSTATUS | MMA | MMASTATUS | AMA | AMASTATUS | AMAVERSION |
|---|---|---|---|---|---|---|---|---|---|
| comp-01 | uksouth | rg-app-01 | Windows | VM deallocated | MicrosoftMonitoringAgent | Succeeded | AzureMonitorWindowsAgent | Succeeded | 1 |
| comp-02 | uksouth | rg-app-01 | Windows | VM running | MicrosoftMonitoringAgent | Succeeded | AzureMonitorWindowsAgent | Succeeded | 1 |
| comp-03 | uksouth | rg-app-01 | Windows | VM running | MicrosoftMonitoringAgent | Succeeded | AzureMonitorWindowsAgent | Succeeded | 1 |
| comp-04 | ukwest | rg-app-01 | Windows | VM running | MicrosoftMonitoringAgent | Succeeded | AzureMonitorWindowsAgent | Succeeded | 1 |
| comp-05 | uksouth | rg-app-01 | Windows | VM running | MicrosoftMonitoringAgent | Succeeded | AzureMonitorWindowsAgent | Succeeded | 1 |
| comp-06 | ukwest | rg-app-01 | Windows | VM running | MicrosoftMonitoringAgent | Succeeded | AzureMonitorWindowsAgent | Succeeded | 1 |
| comp-07 | uksouth | rg-app-01 | Windows | VM running | MicrosoftMonitoringAgent | Succeeded | AzureMonitorWindowsAgent | Succeeded | 1 |
| comp-08 | uksouth | rg-app-01 | Windows | VM running | MicrosoftMonitoringAgent | Succeeded | AzureMonitorWindowsAgent | Succeeded | 1 |
✔️ Conclusion
In this post, we've extended our Resource Graph query to include the extensions for the AMA agent. We've also combined the results for both MMA and AMA to gain a comprehensive overview of all the virtual machines and their respective reporting agents. Hopefully, this will help you to understand the current layout of your environment and which agents you need to transition from MMA to AMA. Please feel free to reach out to me if you have any questions or brainstorming ideas. I'm always happy to help!