There are few questions how to understand Azure Stack Platform Manages Identity and Security. In this article, You will learn about Azure Stack Identity ways. For instance, when your customer logging into the Azure Stack Portal, they should have accessed to their resources. For this reason, you must understand how identity and authentication work in Azure Stack.
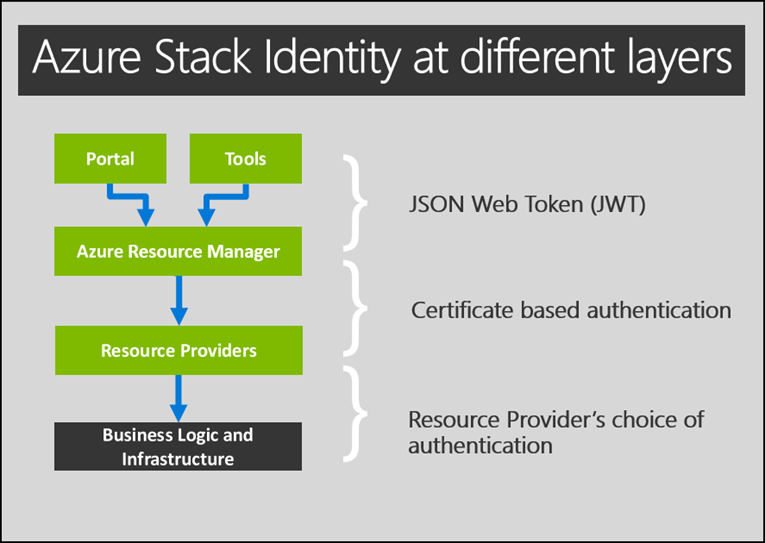
Identity Providers accessible in Azure Stack
Azure Stack generally uses well-known Identity Providers to authenticate an end-user or client. Azure Stack passes a security token to the Identity Providers, which end users can use to access resources for which they have been granted permissions. After Azure Stack will have trusted the supplier of the security token
Some of them are ( Identity Providers List )
- Windows Live ID
- WS-Federation
- Yahoo
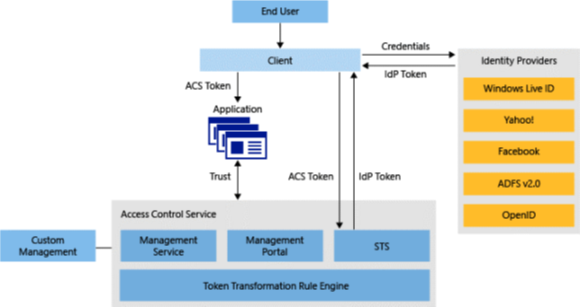
As you can see, Both Azure and Azure Stack use the Access Control Service (ACS) to manage the authentication process. To help understand this process, review the following Access Control Service architecture diagram.
Presently, Azure Stack is supporting the following Identity Providers:
- Active Directory Federation Services (AD FS)
- Azure Active Directory (Azure AD)
If you installed an Azure Stack, you will see an Active Directory domain is installed as part of your Azure Stack Environment. This Active Directory can use to provide authentication to the hosts and virtual machines that make up the Azure Stack infrastructure. Nevertheless, authentication with this domain does not provide access to the Azure Stack Portals from either a cloud operator or user perspective. To obtain access to Azure Stack, you must have an identity in the trusted identity management solution. However, just having an identity does not necessarily give you access to resources. For example, your account "hasan@hasangural.com" is an Azure AD account, and this Azure AD account is associated with an Azure Stack subscription. Unless your account has been given access to a subscription, you will not be able to access any resources.
If I want to use these services, what will happen?
Active Directory Federation Services
Firstly, This Lovely Service used to a lot of services including the third party. If you need to authenticate to the Azure Stack infrastructure using your organization's Active Directory identities, you have to configure AD FS between your organization's AD DS and Azure Stacks Active Directory. As you know, It will be an extra cost. ( Cert, Maintenance, Monitoring. Etc ). One of the benefits of using AD FS is that your organization's infrastructure engineers can use their existing credentials to sign in and manage the Azure Stack environment. They should configure their AD FS Services. An AD FS relying on party trust between the AD in Azure Stack and the AD DS in your organization is used to handle the authentication process. However, using AD FS gives you no permissions to access the Azure Stack Infrastructure AD domain. Anyway, It should not be forgotten that "Azure Stack requires Windows Server 2016 AD FS."
Azure Active Directory Services
As you know, Azure AD is the cloud-based identity management solution provided by Microsoft and is hosted in Azure. However, If you used to Office 365, you have an experience that services. It can have identities that have been solely created in the Azure AD or have identities synchronized from the traditional AD domain.
By using Azure AD identities that have been synchronized from an AD domain, you can choose how to authenticate the users:
- Same Sign-On: Using Azure AD Connect, which synchronizes the identities from AD Domain Services to Azure AD, you can choose to additionally synchronize identity passwords too. This allows users to use the same username and password to authenticate with Azure AD as they do with AD DS.
- Single Sign-On: Instead of using the same password to authenticate users, this option enables the authentication of the identity to occur either through an AD FS infrastructure associated with Azure AD and AD DS or with pass-through authentication.
Multi-Factor Authentication
If you need to configure Multi-Factor authentication, you can do this. You will configure AD FS and Azure AD to utilize Multi-Factor Authentication. The Claims Provider, which could be either AD FS or Azure AD, handles Multi-Factor Authentication outside of the Azure Stack environment.
The following each section, I want to explain.
- Internet connectivity required: For Azure AD-based authentication, Azure Stack requires access to the Internet to authenticate an identity with Azure AD. The Azure AD authentication process then commences either through Same Sign-On or Single Sign-on. AD FS does not require Internet access, provided the Claims Provider can be contacted without having to traverse the Internet. With AD FS, it is the responsibility of the Claims Provider to provide the authentication token to Azure Stack.
- Multi-Tenant: When you configure Azure Stack to use Azure AD for authentication, the cloud operator identity is authenticated with a single Azure AD instance. However, tenant identities can be authenticated from several different Azure AD instances if required. Using AD FS-based identity management, only a single tenant domain can be used as the relying party trust and can only be configured to use a single AD FS Claims Provider
- Fully disconnected: Because Azure AD-based authentication requires Internet access to authenticate identities, you cannot use Azure AD-based authentication in a fully disconnected scenario. AD FS does not require Internet access
- Marketplace Syndication: Regardless of which identity management option you choose, you can use marketplace syndication. However, in an AD FS scenario, the Azure Stack deployment cannot be operating in a fully disconnected scenario.
- Multi-Factor Authentication: You can choose whether or not to use Multi-Factor Authentication outside of Azure Stack. You can configure the identity management solution, irrespective of whether it is Azure AD or AD FS, to utilize Multi-Factor Authentication if required
In sum up, If you are Azure Stack Operator and Cloud Engineer, you should think deeply. Because, you know customers might get you interesting request.