In the previous blog post, we have covered how to create a deploymentScript resource with Bicep. In this blog post, we will continue with the deployment script and talk about how to execute the script for accesing a private network from the deployment script.
👉 Accessing a private network from the deployment script
Imagine that you have a scenario where you have resources they locked down to a private network and you need to access them from your deployment script. In this case, you can use the deploymentScripts resource to run a script that accesses the private network.
⚙️ Deployment script structure for accessing a private network
To access a private network from your deployment script, you need to ensure that the script runs in a container that has access to the private network. Here's how you can set up the deploymentScripts resource to run a script that accesses a private network:
We will need to add new properties to the deploymentScripts resource:
- Managed Identity must have at least
Storage File Data Privileged Contributorrole to access the storage account. Role assignment can be done in the Bicep. -
properties.storageAccountSettings: This is where you define the storage account your script will interact with. Think of it as your script’s home base within the operation. -
properties.containerSettings: We need to set subnetId for the container to access the private network.
⚗️ Close look at storage account and subnet
Storage Account
resource helloFriendStorageAcc 'Microsoft.Storage/storageAccounts@2023-01-01' = {
name: hfStorageAccName
location: location
sku: {
name: 'Standard_LRS'
}
kind: 'StorageV2'
properties: {
networkAcls: {
bypass: 'AzureServices'
virtualNetworkRules: [
{
// Allow the subnet to access the storage account
id: subnet.id
action: 'Allow'
state: 'Succeeded'
}
]
defaultAction: 'Deny'
}
}
}
Subnet for the container
resource helloFriendVnet 'Microsoft.Network/virtualNetworks@2023-05-01' = {
name: helloFriendVNName
location: location
properties: {
addressSpace: {
addressPrefixes: [
'10.0.0.0/16'
]
}
enableDdosProtection: false
subnets: [
{
name: helloFriendSubnetName
properties: {
addressPrefix: '10.0.0.0/24'
serviceEndpoints: [
{
service: 'Microsoft.Storage'
}
]
delegations: [
{
// This is required for the container to access the private network
// Delegate the subnet to the container instance service
name: 'Microsoft.ContainerInstance.containerGroups'
properties: {
serviceName: 'Microsoft.ContainerInstance/containerGroups'
}
}
]
}
}
]
}
}
📝 Full Bicep template
resource helloFriendDeploymentScript 'Microsoft.Resources/deploymentScripts@2020-10-01' = {
name: 'helloFriendDeploymentScript'
location: resourceGroup().location
kind: 'AzurePowerShell'
identity: {
type: 'UserAssigned'
userAssignedIdentities: {
'/subscriptions/01234567-89AB-CDEF-0123-456789ABCDEF/resourcegroups/deploymenttest/providers/Microsoft.ManagedIdentity/userAssignedIdentities/myscriptingid': {}
}
}
properties: {
azPowerShellVersion: '3.0'
storageAccountSettings: {
storageAccountName: helloFriendStorageAcc.name
}
containerSettings: {
subnetIds: [
{
id: vnet:: helloFriendVnet.subnets[0].id
}
]
}
scriptContent: '''
$resourceGroupName = 'myResourceGroup'
$networkManagerName = 'myNetworkManager'
$getNetworkManager = Get-AzNetworkManager -ResourceGroupName $resourceGroupName -Name $networkManagerName -ErrorAction Stop
Write-output "Network Manager $networkManagerName exists in resource group." -Level Info
$DeploymentScriptOutputs = @{}
$DeploymentScriptOutputs['Id'] = ($getNetworkManager.id)
'''
retentionInterval: 'P1D'
}
}
All set! Now you we can run bicep template to deploy the deployment script to access a private network. After we deploy a deployment script resource, the resource is listed under the resource group in the Azure portal. The Overview page lists the two supporting resources in addition to the deployment script resource. The supporting resources will be deleted after the retention interval expires.
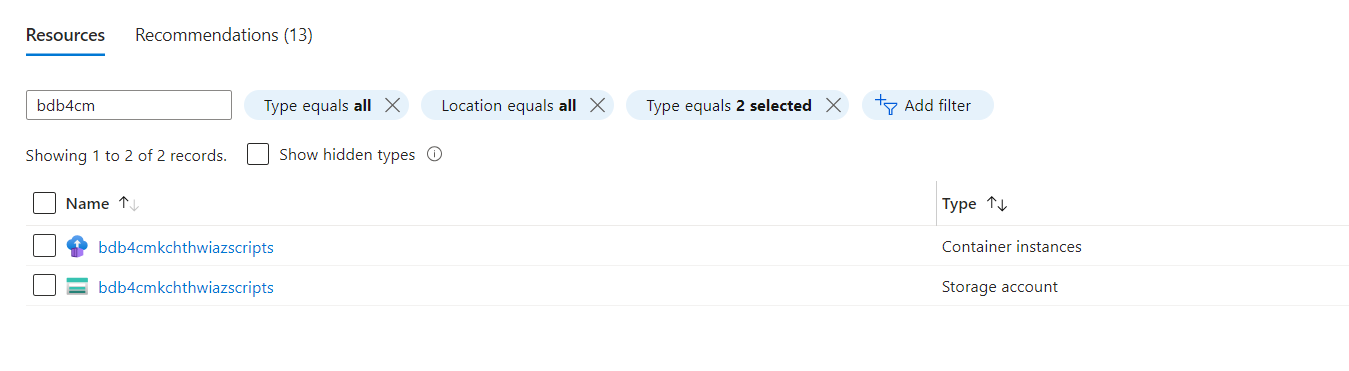
Notice that both supporting resources have the azscripts suffix in their names because these resources are created automatically. The other way to identify the supporting resources is by using tags.Select the deployment script resource from the list. The Overview page of a deployment script resource displays important information about the resource, such as Provisioning state and the two supporting resources (Storage account and Container instance). The Logs area shows the print text from the script.
📝 Summary for Deployment Scripts
By leveraging Deployment Scripts, we extend our automation capabilities within Azure, ensuring that even the most intricate tasks can be handled efficiently and securely. Whether it’s a simple configuration change or a complex series of operations within a Virtual Network, Deployment Scripts provide the flexibility and power to get the job done.
Thanks for reading trough the blog post