Many organizations seek to understand the cost impact when they want to use Azure Defender For Cloud (ADfC). I have been working on price estimates when I need to enable Azure Defender for Cloud services for specific resources in a tenant. However, I developed a PowerShell script that estimates the overall cost according to the ADfC resource coverage per subscription that does not include all estimation options.
Microsoft recently released a new Price Estimation Dashboard using the Azure Resource Graph and Resource metrics in order to provide a forecast for the candidate of ADfC Customers.
📄Introducing the ADfC Price Estimation Dashboard
When you deploy the workbook in your subscriptions, it will have an overview page that shows your overall enablement of Azure Defender for Cloud. That page will give you insights into your unique or all subscriptions. You can also filter multiple subscriptions.
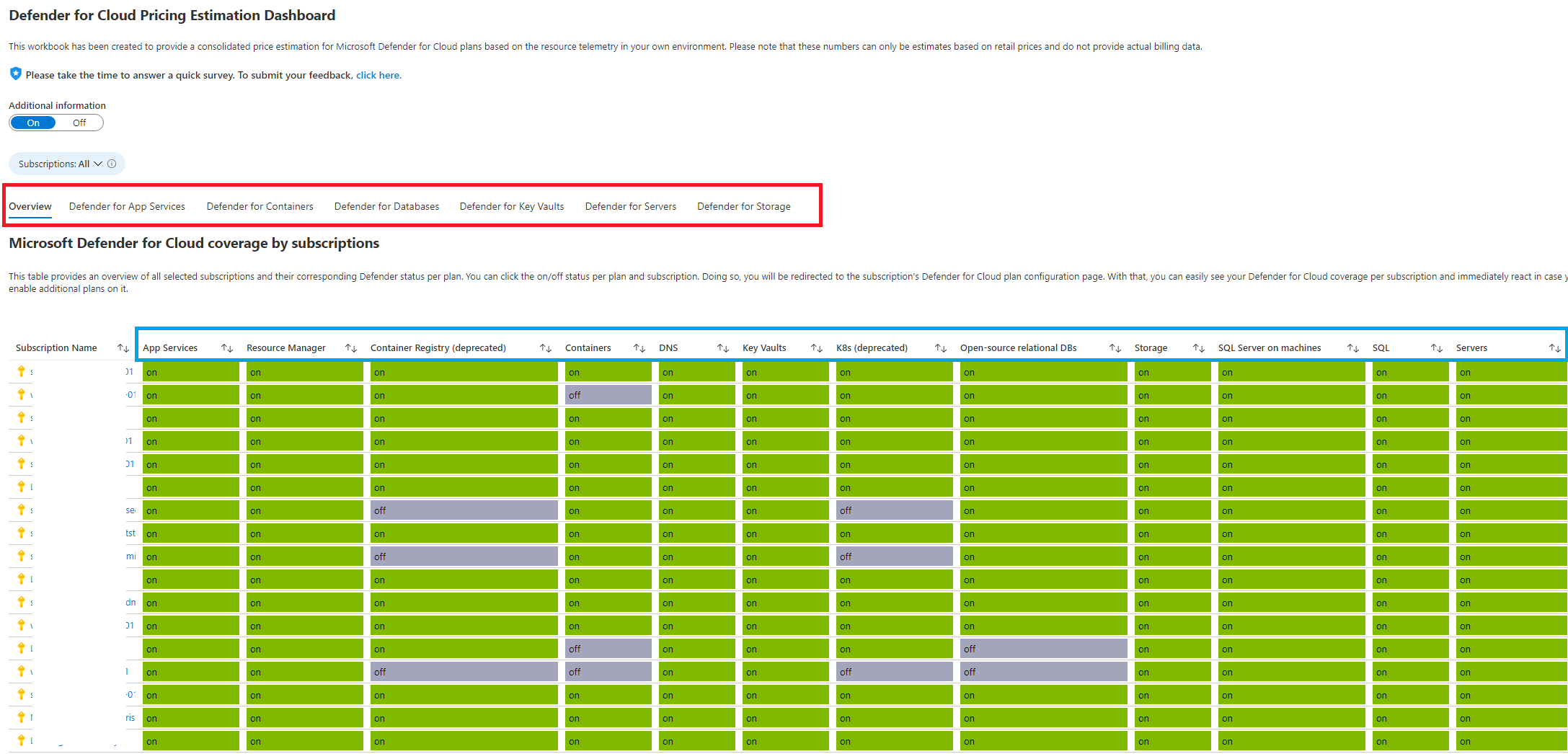
As you can see above, the area shows as greyed out if the plan is not enabled. If the plan is activated, the area is shown as green. You might want to confirm also existing configuration settings in the Azure Defender for Cloud in Azure Portal blade, don't worry, it is pretty simple. Just click on the specific on/off values in the table then it will redirect you to the ADfC blade for enabling or disabling existing plans.
⚡Is this paid service ?
No, it is completely free and you are not required to be a paid customer of Azure Defender for Cloud (ADfC).
🧑💻How to get the ADfC Price Estimation Dashboard
Before you deploy the workbook, bear in mind the following plans are covered in the workbook:
- Microsoft Defender for App Services
- Microsoft Defender for Containers
- Microsoft Defender for Key Vaults
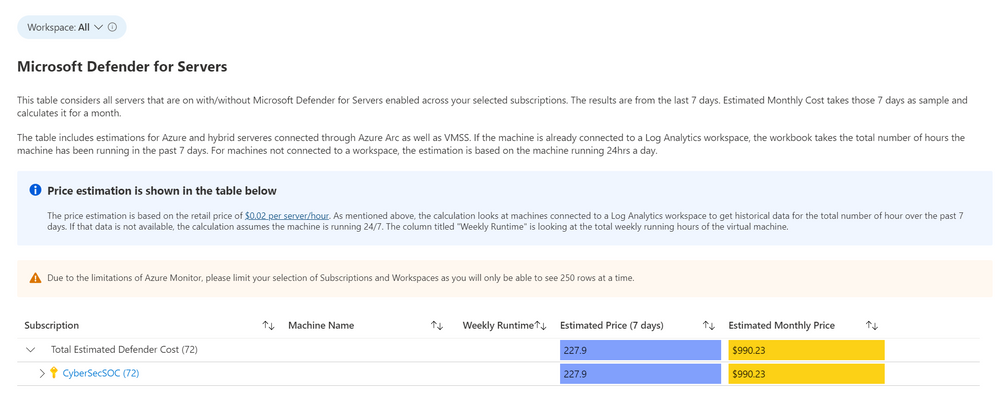
- Microsoft Defender for Servers
- Microsoft Defender for Storage
- Microsoft Defender for Databases (including SQL PaaS, SQL on machines, open-source relational databases)
⚓Option 1: Deploy it from GitHub Template
Once you click the Deploy To Azure button above, you will see that page redirects you to Azure Portal. You will require to complete deployment parameters to create a Microsoft Workbook for your organization.
⚓Option 2: Deploy it from Azure PowerShell
# --- Set resource group name and create
$ResourceGroupName = "rg-ukw-adfc-dashboard"
$subscriptionName = "<your-subscription-name>"
Set-AzContext -Subscription $subscriptionName
New-AzResourceGroup -Name $ResourceGroupName -Location "UK West" -Force
# --- Deploy infrastructure
$DeploymentParameters = @{
workbookDisplayName = "Microsoft Defender for Cloud Price Estimation"
workbookType = "workbook"
workbookSourceId = "Azure Security Center"
workbookId = "[newGuid()]"
}
New-AzResourceGroupDeployment -Name "adfc-deplyoment-01" -ResourceGroupName $ResourceGroupName `
-TemplateUri "https://raw.githubusercontent.com/Azure/Microsoft-Defender-for-Cloud/main/Workbooks/Microsoft%20Defender%20for%20Cloud%20Price%20Estimation/azuredeploy.json" @DeploymentParameters
🎉(Bonus) Option 3: Using Custom PowerShell Script for estimation Report
function Get-ADfCPriceEstimation {
$getSubs = (Search-AzGraph -Query "resourcecontainers
| where type == 'microsoft.resources/subscriptions'
| mv-expand state=properties.state
| where state == 'Enabled'
| project name, Id=subscriptionId, state") | Select-Object -First 3
$planReport = @();
ForEach ($sub in $getSubs) {
Set-AzContext -Subscription $sub.Id | Out-Null
$getVMCount = (Search-AzGraph -Query "resources
| where subscriptionId == '$($sub.Id)'
| where type =~ 'Microsoft.Compute/virtualMachines'
| summarize count() ").count_
$getSQLVMCount = (Search-AzGraph -Query "resources
| where subscriptionId == '$($sub.Id)'
| where type =~ 'microsoft.sqlvirtualmachine/sqlvirtualmachines'
| summarize count() ").count_
$getPaaSSQLCount = (Search-AzGraph -Query "resources
| where subscriptionId == '$($sub.Id)'
| where type == 'microsoft.sql/servers'
| summarize count()").count_
$getAppServiceCount = (Search-AzGraph -Query "resources
| where subscriptionId == '$($sub.Id)'
| where type == 'microsoft.web/sites'
| summarize count()").count_
$getStorageCount = (Search-AzGraph -Query "resources
| where subscriptionId == '$($sub.Id)'
| where type == 'microsoft.storage/storageaccounts'
| summarize count()").count_
$getK8sCount = (Search-AzGraph -Query "resources
| where subscriptionId == '$($sub.Id)'
| where type == 'microsoft.containerservice/managedclusters'
| summarize count()").count_
$getRegistryCount = (Search-AzGraph -Query "resources
| where subscriptionId == '$($sub.Id)'
| where type == 'microsoft.containerregistry/registries'
| summarize count()").count_
$getKVCount = (Search-AzGraph -Query "resources
| where subscriptionId == '$($sub.Id)'
| where type == 'microsoft.keyvault/vaults'
| summarize count()").count_
$getDNSCount = (Search-AzGraph -Query "resources
| where subscriptionId == '$($sub.Id)'
| where type == 'microsoft.network/privatednszones'
| summarize count()").count_
$DatabaseCount = (Search-AzGraph -Query "resources
| where subscriptionId == '$($sub.Id)'
| where type == 'microsoft.dbformysql/servers' or type == 'microsoft.dbforpostgresql/servers'
| summarize count()").count_
$CosmosCount = (Search-AzGraph -Query "resources
| where subscriptionId == '$($sub.Id)'
| where type == 'microsoft.documentdb/databaseaccounts'
| summarize count()").count_
$containerCount = (Search-AzGraph -Query "resources
| where subscriptionId == '$($sub.Id)'
| where type == 'microsoft.containerinstance/containergroups'
| summarize count()").count_
$getSecPlans = Get-AzSecurityPricing
$secObj = [PSCustomObject]@{
SubscriptionName = $sub.Name
SubscriptionId = $sub.Id
VirtualMachines = ($getSecPlans | Where-Object { $PSItem.Name -eq "VirtualMachines" }).PricingTier
CountVirtualMachines = $getVMCount
SqlServers = ($getSecPlans | Where-Object { $PSItem.Name -eq "SqlServers" }).PricingTier
CountSqlServers = $getPaaSSQLCount
AppServices = ($getSecPlans | Where-Object { $PSItem.Name -eq "AppServices" }).PricingTier
CountAppServices = $getAppServiceCount
StorageAccounts = ($getSecPlans | Where-Object { $PSItem.Name -eq "StorageAccounts" }).PricingTier
CountStorageAccounts = $getStorageCount
SqlServerVirtualMachines = ($getSecPlans | Where-Object { $PSItem.Name -eq "SqlServerVirtualMachines" }).PricingTier
CountSQLServerVirtualMachines = $getSQLVMCount
KubernetesService = ($getSecPlans | Where-Object { $PSItem.Name -eq "KubernetesService" }).PricingTier
CountKubernetesService = $getK8sCount
ContainerRegistry = ($getSecPlans | Where-Object { $PSItem.Name -eq "ContainerRegistry" }).PricingTier
CountContainerRegistry = $getRegistryCount
KeyVaults = ($getSecPlans | Where-Object { $PSItem.Name -eq "KeyVaults" }).PricingTier
CountKeyVaults = $getKVCount
Dns = ($getSecPlans | Where-Object { $PSItem.Name -eq "Dns" }).PricingTier
CountDNS = $getDNSCount
OpenSourceRelationalDatabases = ($getSecPlans | Where-Object { $PSItem.Name -eq "OpenSourceRelationalDatabases" }).PricingTier
CountOpenSourceReleationDatabes = $DatabaseCount
CosmosDbs = ($getSecPlans | Where-Object { $PSItem.Name -eq "CosmosDbs" }).PricingTier
CountCosmosDB = $CosmosCount
Containers = ($getSecPlans | Where-Object { $PSItem.Name -eq "Containers" }).PricingTier
CountContainers = $containerCount
}
$planReport += $secObj
}
return $planReport
}
Get-ADfCPriceEstimation | ConvertTo-Csv | Out-Null '<Please-Put-Path>'