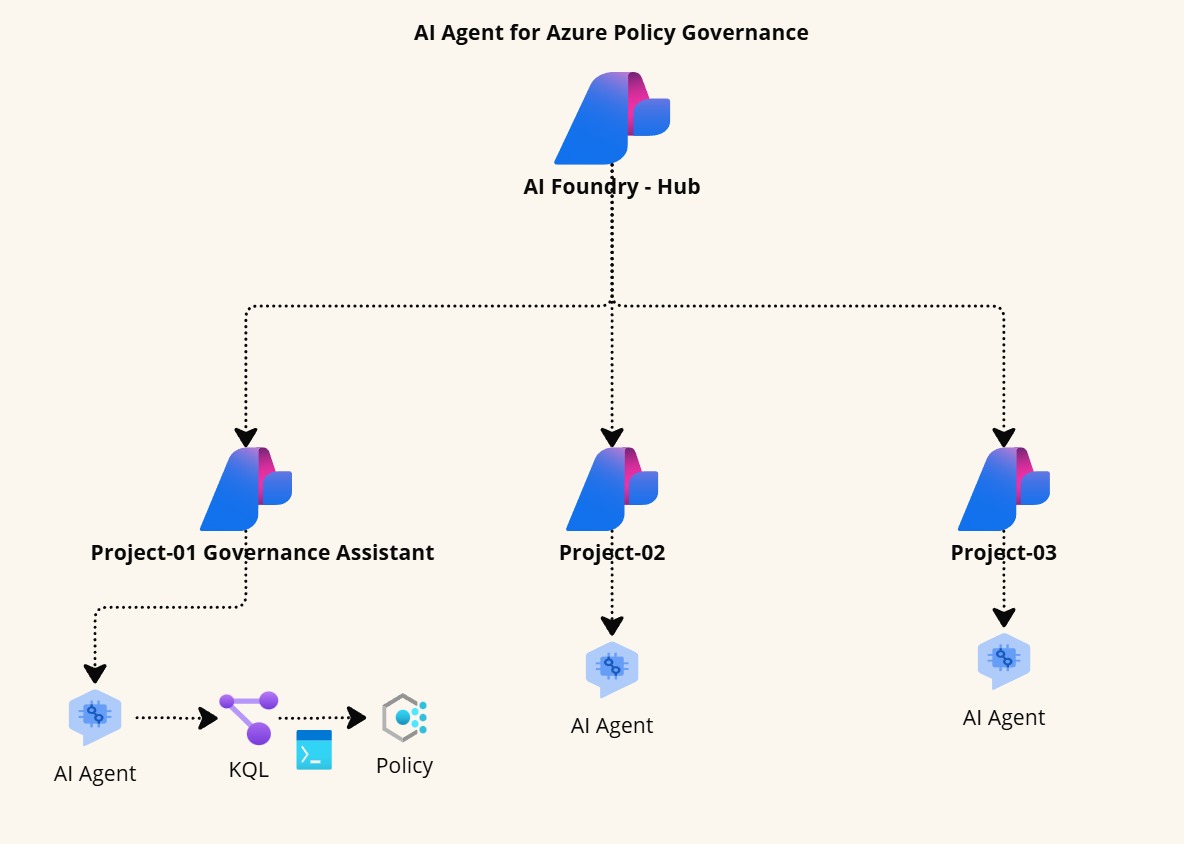
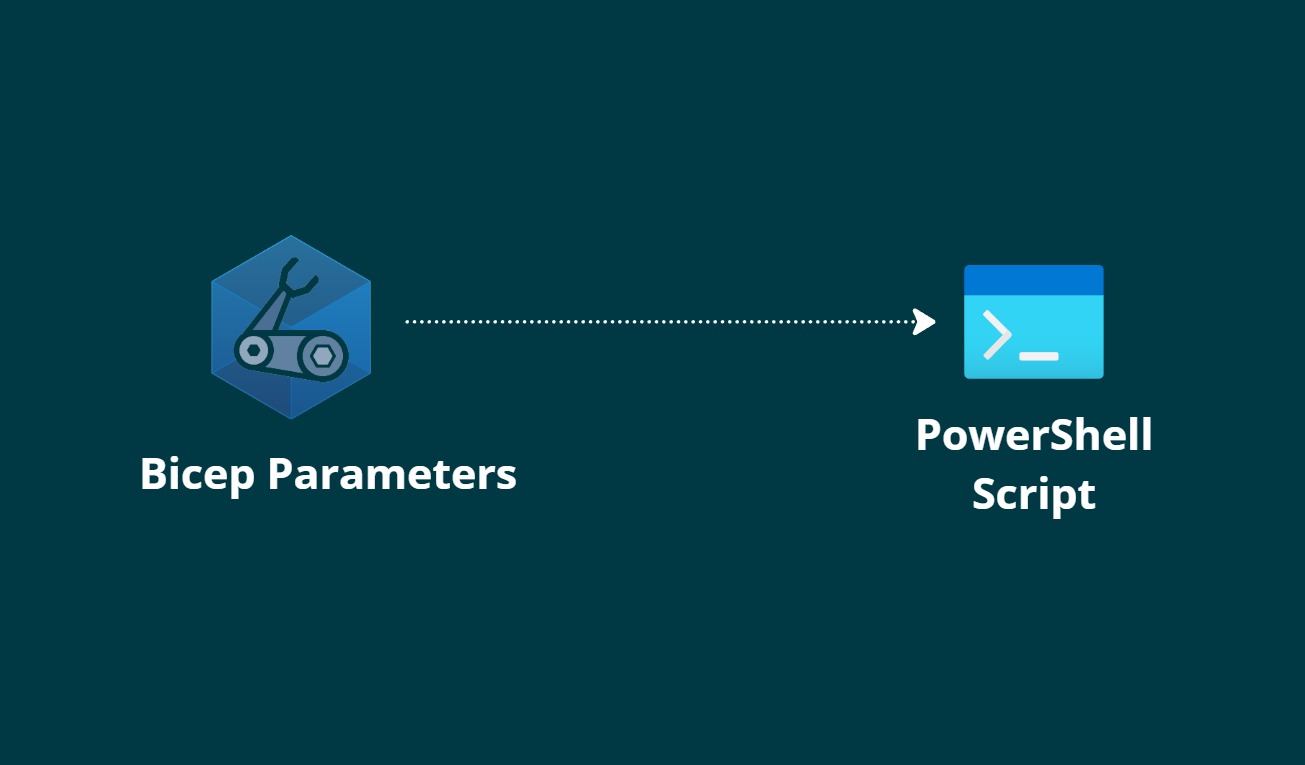
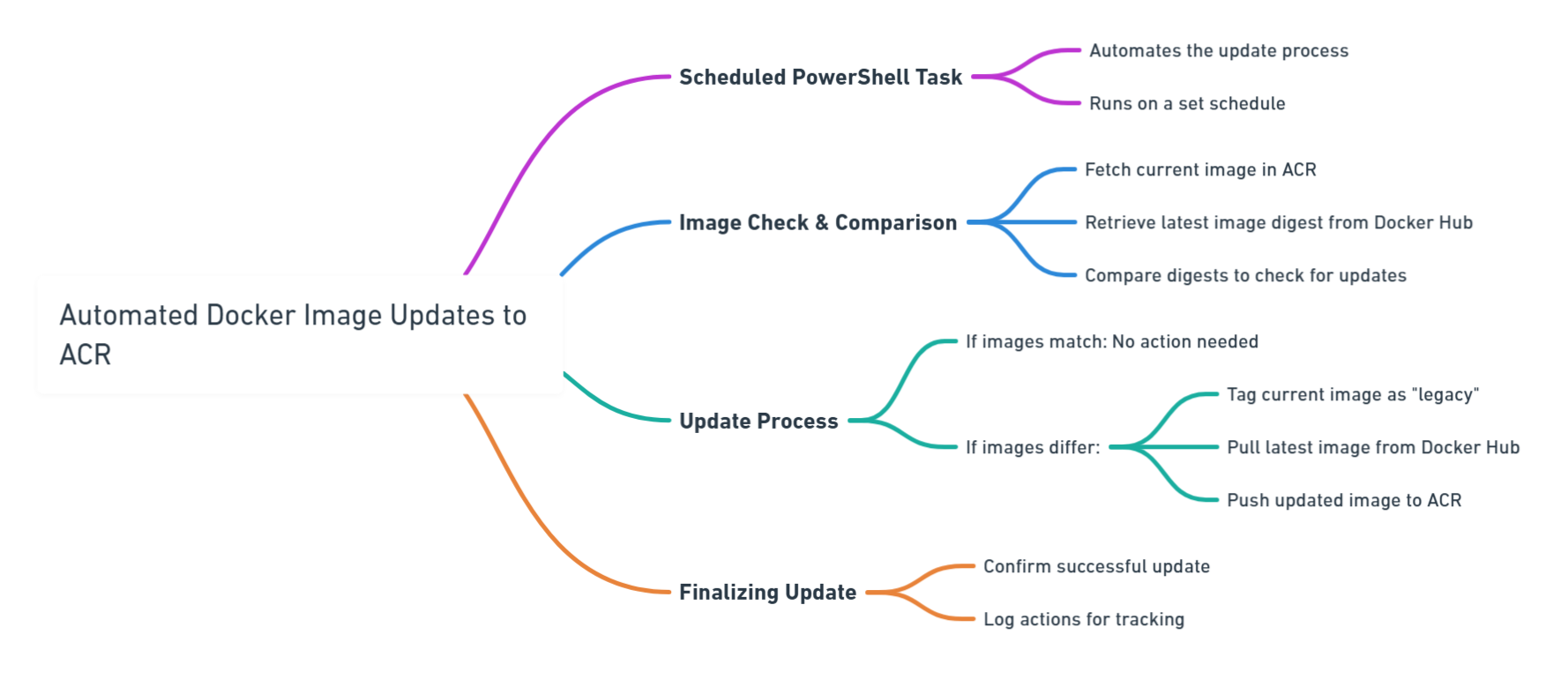
I'm excited to announce that, continuing my journey since 2017, I will be speaking at the Azure Global Bootcamp 2025 on May 8- 10. This year, I’m eager to share more insights and learnings with the Azure community. Join me as we dive into the latest Azure advancements and tackle current tech challenges together.