In our last article, I tried to explain how we can get a report for Secure Score details and assignments of Defender for Cloud Plans for each subscription. I will now expand these type of queries mainly for Virtual Networks.
If you are managing multiple Azure Hub environments, at some point, you will need to report the status of Virtual Network Peerings as well as Peering Flags for the connectivity side of it. As we said before, there are various ways to obtain it. If you have over a hundred subscriptions, I wouldn't prefer to use PowerShell for these types of reports for generating them. In my personal opinion, Azure Resource Graph is a solid and decent way to get results as an object in PowerShell, and then you can use data for generating HTML, CSV, Table Storage or updating SQL Table.
🌠Virtual Network Peering Report for All Subscriptions.
You can find Virtual Network and Peering details in resources/virtualNetworks. Later on, you can get the information that you wanted in a table with every property.
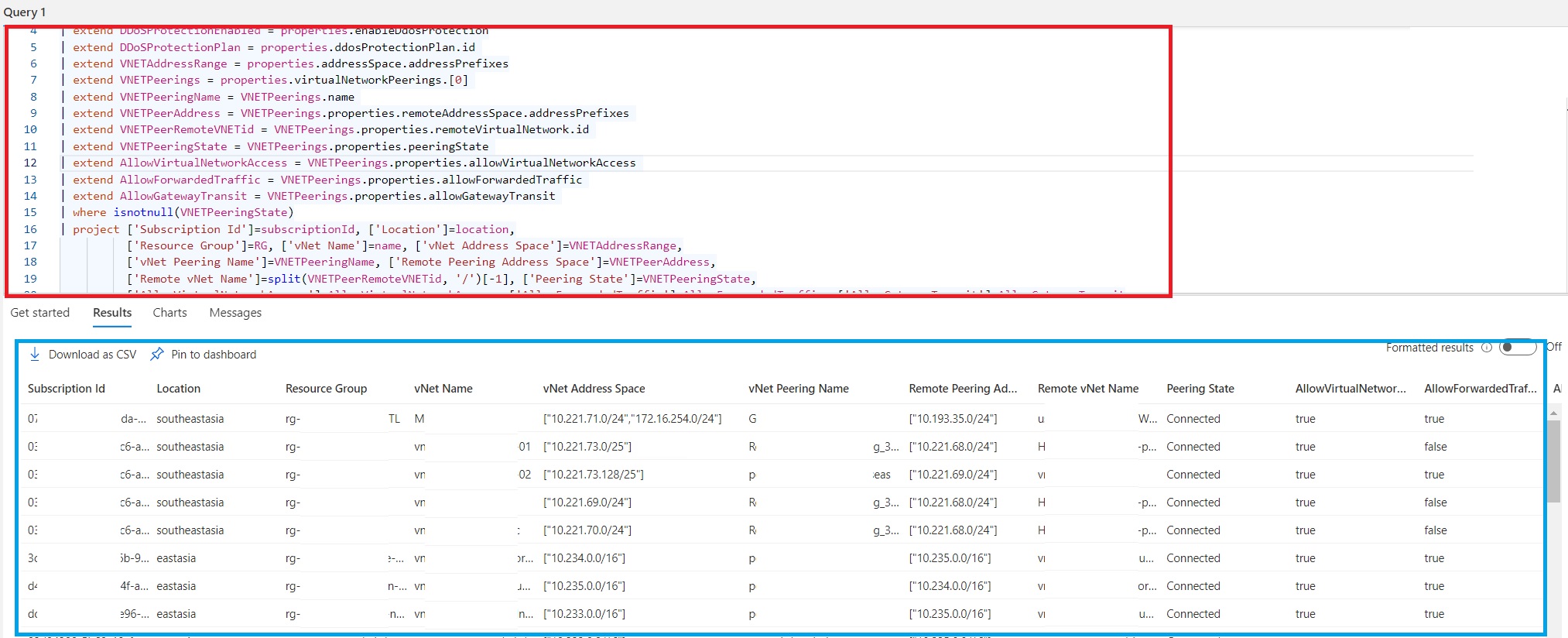
Resources
| where type contains "virtualNetworks"
| extend RG = split(substring(id, 0, indexof(id, '/providers')),'/')[-1]
| extend DDoSProtectionEnabled = properties.enableDdosProtection
| extend DDoSProtectionPlan = properties.ddosProtectionPlan.id
| extend VNETAddressRange = properties.addressSpace.addressPrefixes
| extend VNETPeerings = properties.virtualNetworkPeerings.[0]
| extend VNETPeeringName = VNETPeerings.name
| extend VNETPeerAddress = VNETPeerings.properties.remoteAddressSpace.addressPrefixes
| extend VNETPeerRemoteVNETid = VNETPeerings.properties.remoteVirtualNetwork.id
| extend VNETPeeringState = VNETPeerings.properties.peeringState
| extend AllowVirtualNetworkAccess = VNETPeerings.properties.allowVirtualNetworkAccess
| extend AllowForwardedTraffic = VNETPeerings.properties.allowForwardedTraffic
| extend AllowGatewayTransit = VNETPeerings.properties.allowGatewayTransit
| where isnotnull(VNETPeeringState)
| project ['Subscription Id']=subscriptionId, ['Location']=location,
['Resource Group']=RG, ['vNet Name']=name, ['vNet Address Space']=VNETAddressRange,
['vNet Peering Name']=VNETPeeringName, ['Remote Peering Address Space']=VNETPeerAddress,
['Remote vNet Name']=split(VNETPeerRemoteVNETid, '/')[-1], ['Peering State']=VNETPeeringState,
['AllowVirtualNetworkAccess']=AllowVirtualNetworkAccess, ['AllowForwardedTraffic']=AllowForwardedTraffic,
['AllowGatewayTransit'=AllowGatewayTransit
Here is the example of report you can see below for the query above.
🌠Usage of Private Endpoints in all subscriptions.
Let's dive into another topic, assume that your organization has been using Private Endpoints at some point. You are asked to identify whichever Private Endpoints use, which vNet and Subnet and Resource types. Here is the requested Resource Graph query for generating a report for your environment. You are not required to authenticate in PowerShell or rely on any version. Only need to copy the Resource Graph query from here and then execute it from Resource Graph Explorer, and that's it!
Resources
| where type == "microsoft.network/privateendpoints"
| join kind=inner (
resourcecontainers
| where type == 'microsoft.resources/subscriptions'
| project subscriptionId, subscriptionName = name)
on subscriptionId
| extend RG = split(substring(id, 0, indexof(id, '/providers')),'/')[-1]
| extend NetworkInterfaces = split(properties.networkInterfaces.[0].id, '/')[-1]
| extend Subnet = properties.subnet.id
| extend ManualPrivateLinkServiceConnections = tostring(properties.manualPrivateLinkServiceConnections)
| extend PrivateLinkServiceid = properties.privateLinkServiceConnections.[0].properties.privateLinkServiceId
| extend PrivateLinkServiceGroupids = tostring(properties.privateLinkServiceConnections.[0].properties.groupIds)
| extend PrivateLinkServiceConnections = properties.privateLinkServiceConnections.[0].id
| extend PrivateLinkCustomDNS = tostring(properties.customDnsConfigs)
| project ['Subscription Name']=subscriptionName, ['Subscription Id']=subscriptionId, ['Location']=location,
['Resource Group']=RG, ['Network Interface']=NetworkInterfaces,
['vNet Name of Private Endpoint']=split(Subnet,'/')[8],
['vSubnet Name of Private Endpoint']=split(Subnet,'/')[-1],
['Sub Id of Private Endpoint']=split(PrivateLinkServiceid,'/')[2],
['Name of Private Endpoint']=split(PrivateLinkServiceid,'/')[-1],
['Group Ids of Private Endpoint']=PrivateLinkServiceGroupids,
['Connection Name of Private Endpoint']=split(PrivateLinkServiceConnections,'/')[-1]
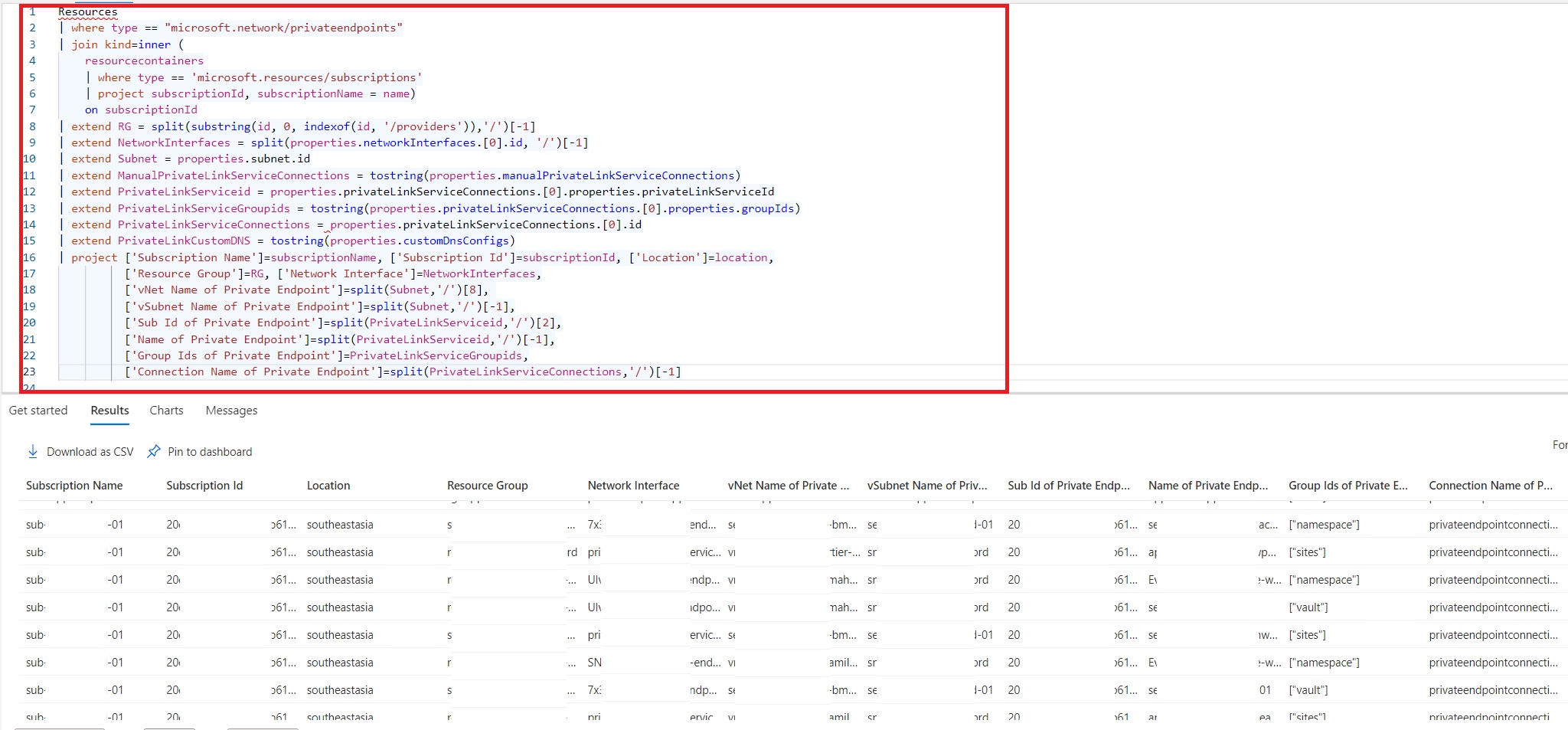
The result above shows us that we can get the usage of Private Endpoints in minutes using KQL queries. If you are seeking to get more example queries then stay tune!