You might be managing a very complex or non-complex environment in your organization. At some point, your organization would probably have Azure Resources such as Public IP Address(s), Network Security Group(s), Traffic Manager, Virtual Network Peerings, VPN Gateway(s), etc.
I have seen this challenge in many Azure Environments. The leading question is, what is the attack surface of my organization, that can be exploited by an attacker. Identifying this type of endpoint can be complex sometimes. For all kind of these questions, we will claim the help of the Network Security Dashboard from Microsoft Azure.
💬Introducing the Network Security Dashboard
The new Network Security Dashboard gives you a single pane of glass view and enhanced visibility into the configuration of your overall cloud networking and network security services for your Azure Environments. The Network Security Dashboard uses two components in Azure:
- 💡Azure Resource Graph for querying your environments.
- 💡Visualizing the results of Resource Graph with Azure Workbooks
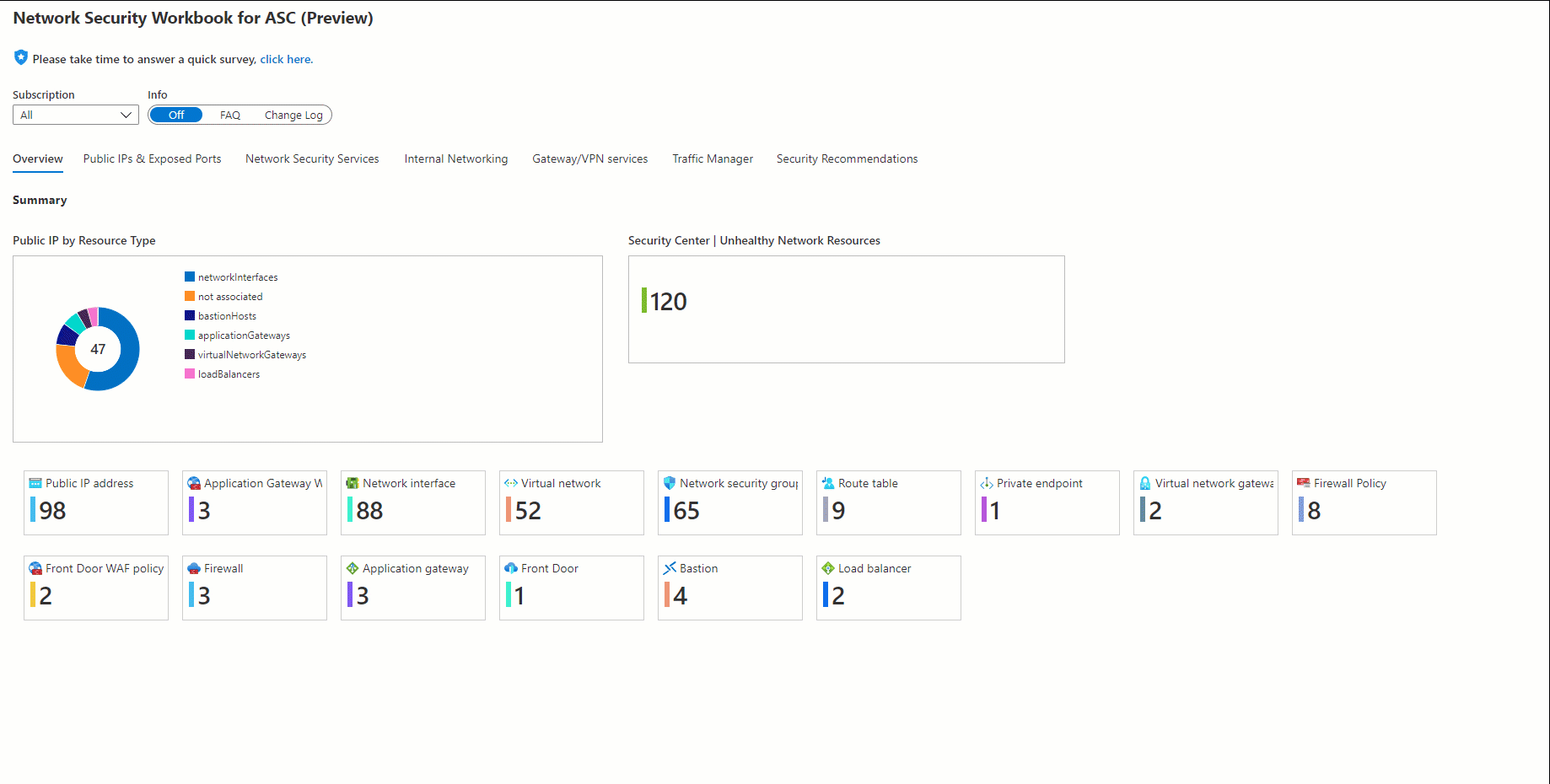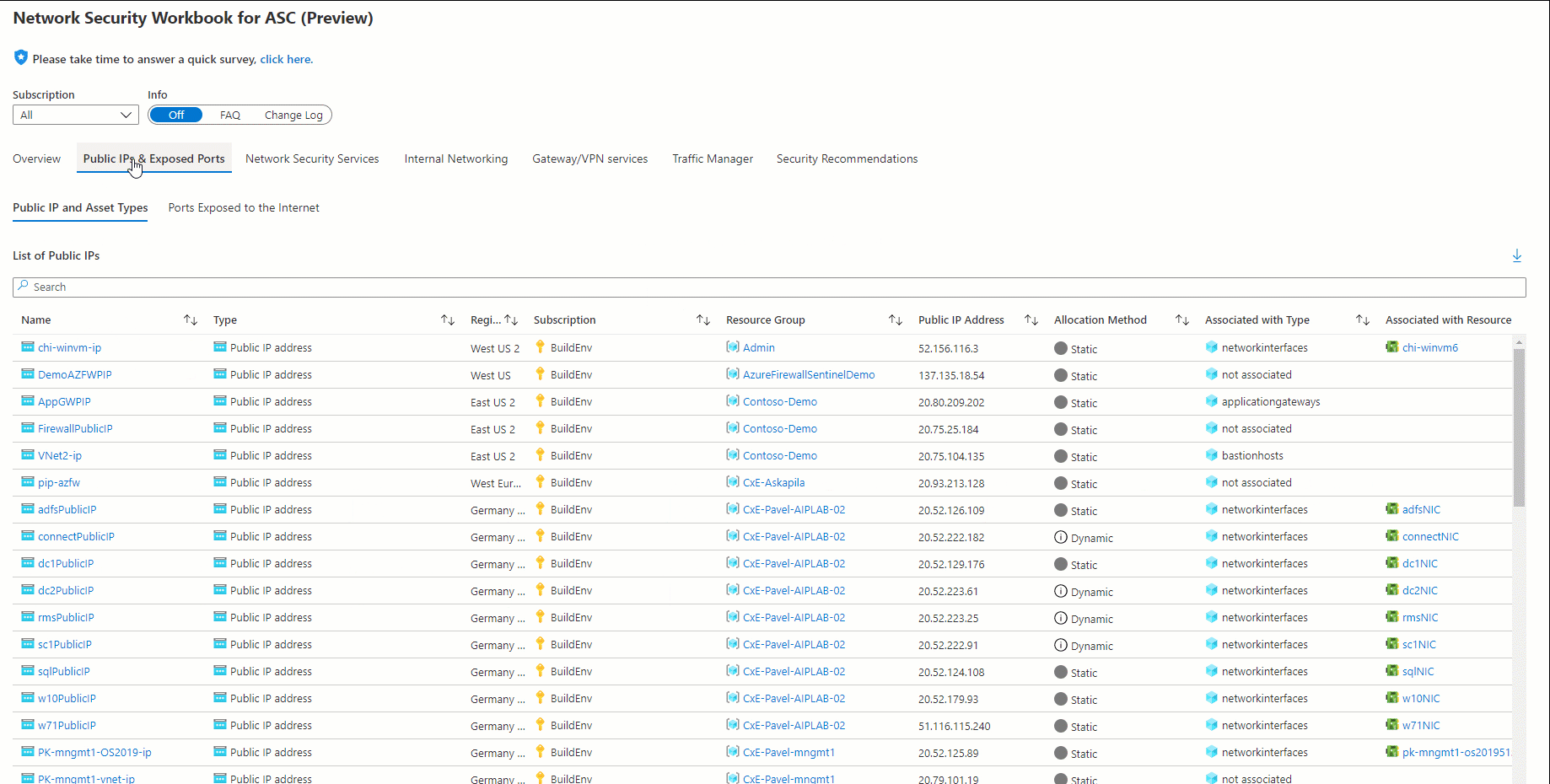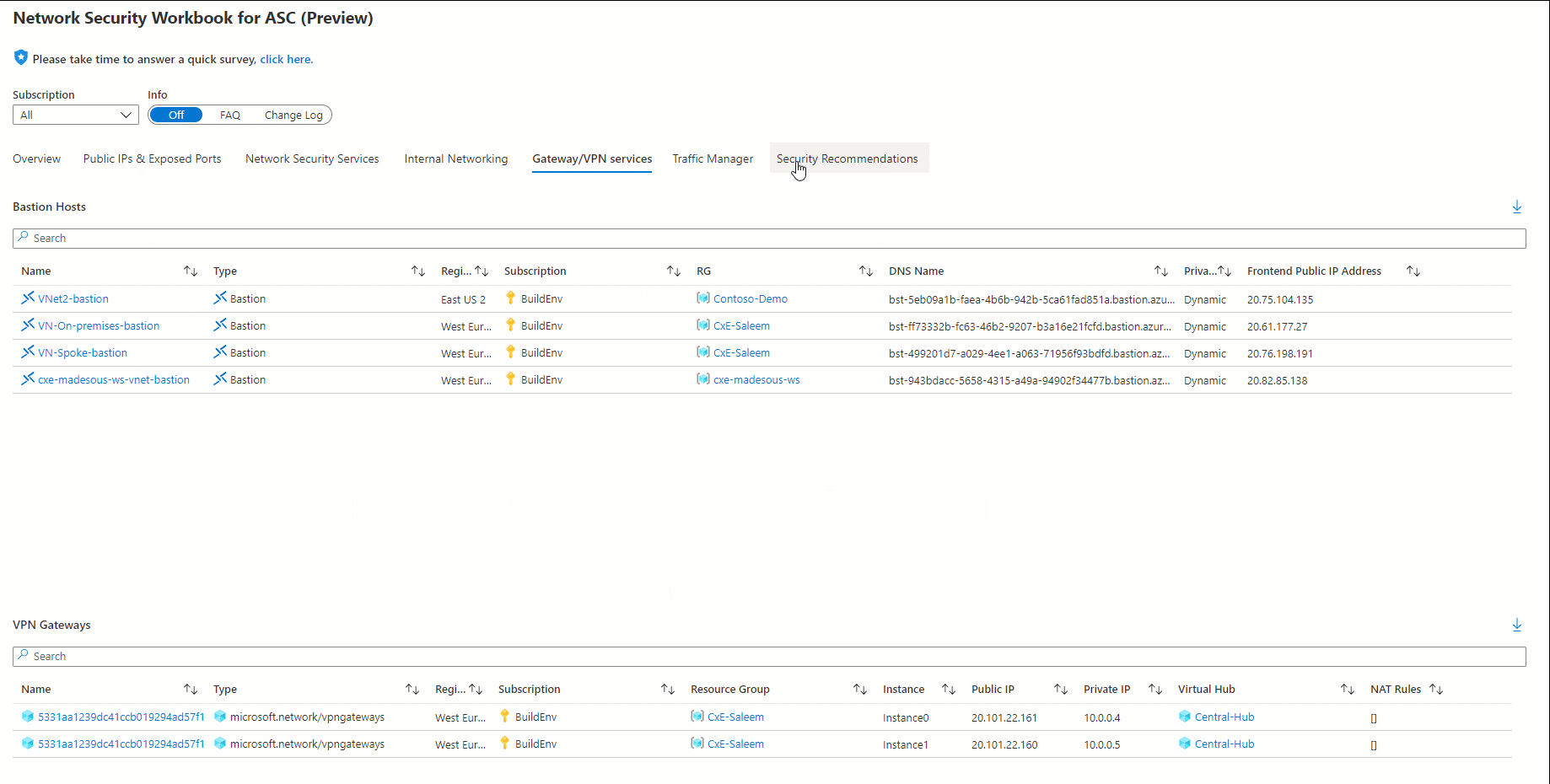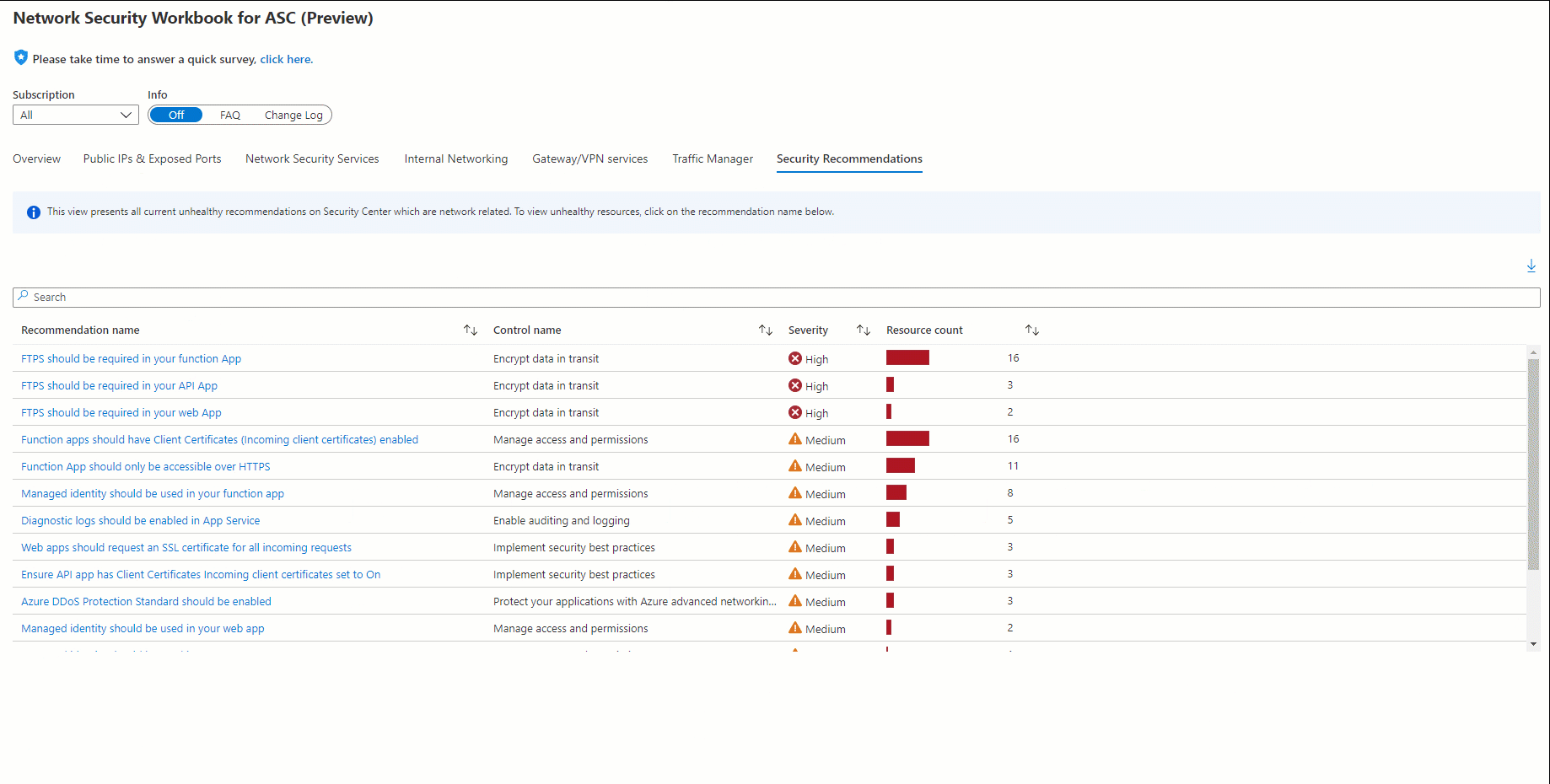
| Section | Intention |
|---|---|
| Public IPs & exposed ports | ports exposed to the internet and mapping of public IPs to asset types |
| Network security services: | DDoS protections plans, Azure Firewall and Firewall policies, Azure WAF policies and NSG views |
| Internal networking mapping | network interfaces, route tables, private links and virtual networks with DDoS protection status |
| Gateway and VPN services: | consolidated view of Bastion hosts, VPN gateways, Virtual Network Gateways and Express Route circuits |
| Traffic Manager | details of all your traffic manager profiles |
| Virtual WAN (vWAN) | consolidated view of Virtual WANs (inlcuding VPN/ExpressRoute/P2S) |
| Security Center recommendations: | related recommendations including resource count, severity, and security control |
| PaaS Services: | ipRules, virtualNetworkRules and privateEndpointConnections for Databases & Storage Accounts & Web Apps and Key Vaults |
⚡Is this a paid service ?
No, it is entirely free, and you are not required to be a paid customer of Azure Defender for Cloud (ADfC).
🧑💻How to get the Network Security Dashboard in your estate
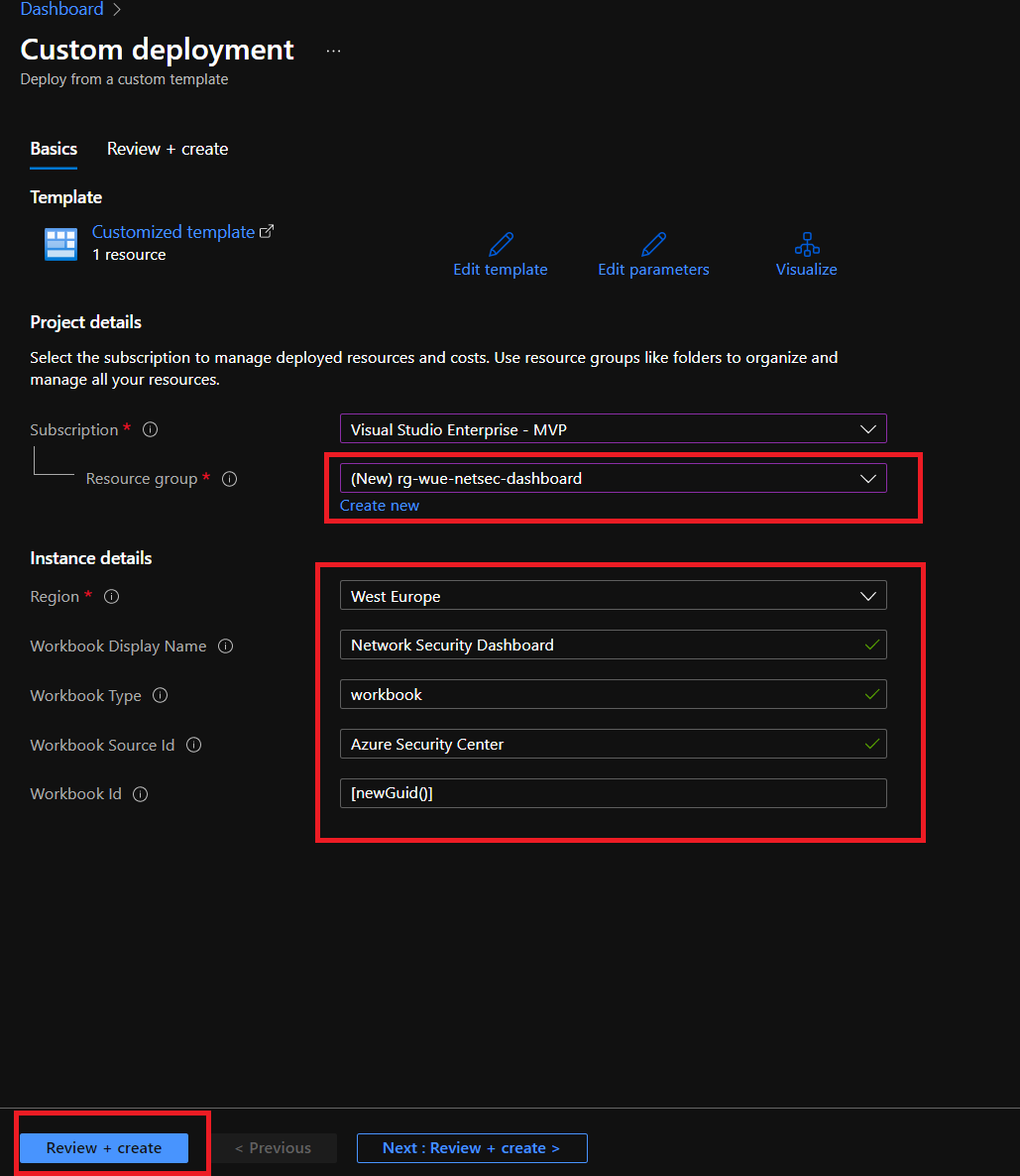
There are various ways to get this Dashboard. You either go to the below GitHub Page to click on the Deploy-to-Azure button or use the PowerShell Script below to provision Azure Workbook in your resource group.
Option 1: Deploy it from GitHub Template
Once you have clicked above the Deploy To Azure button, you will see that page redirects you to Azure Portal. You will require to complete deployment parameters to create a Microsoft Workbook for your organization.
Option 2: Deploy it from Azure PowerShell
# --- Set resource group name and create
$ResourceGroupName = "rg-weu-netsec-dashboard"
$subscriptionName = "<your-subscription-name>"
Set-AzContext -Subscription $subscriptionName
New-AzResourceGroup -Name $ResourceGroupName -Location "UK West" -Force
# --- Deploy infrastructure
$DeploymentParameters = @{
workbookDisplayName = "Network Security Dashboard"
workbookType = "workbook"
workbookSourceId = "Azure Security Center"
workbookId = "[newGuid()]"
}
New-AzResourceGroupDeployment -Name "netsec-deplyoment-01" -ResourceGroupName $ResourceGroupName `
-TemplateUri "https://raw.githubusercontent.com/Azure/Microsoft-Defender-for-Cloud/main/Workbooks/Network%20Security%20Dashboard/armTemplate.json" @DeploymentParameters
After the deployment is completed successfully, you can open Azure Workbook to explore your environment without having a hassle!