We can use Infrastructure as a Code for many distinct purposes. In this article series, we will try to understand how Terraform and Azure FrontDoor provisioning work together and make an end-to-end FrontDoor deployment. You may come across articles that compare FrontDoor and Application Gateway on this blog. FrontDoor is a successful, secure, and convenient load-balancing solution that works on Layer-7 created by Microsoft Azure. It is also used together with Microsoft services such as "Bing, Office 365, Xbox Live, MSN, LinkedIn ve Azure DevOps," and it is indeed incredible to have this infrastructure.

Let's try to understand what we want to do before getting into our terraform module structure example. First of all, an Azure Subscription is a must, and we need to implement a Service Principal configuration alongside it.
- Azure Subscription
- Service Princpal for authenticating to the Subscription.
- Terraform Client
- Visual Code with Terraform Extension
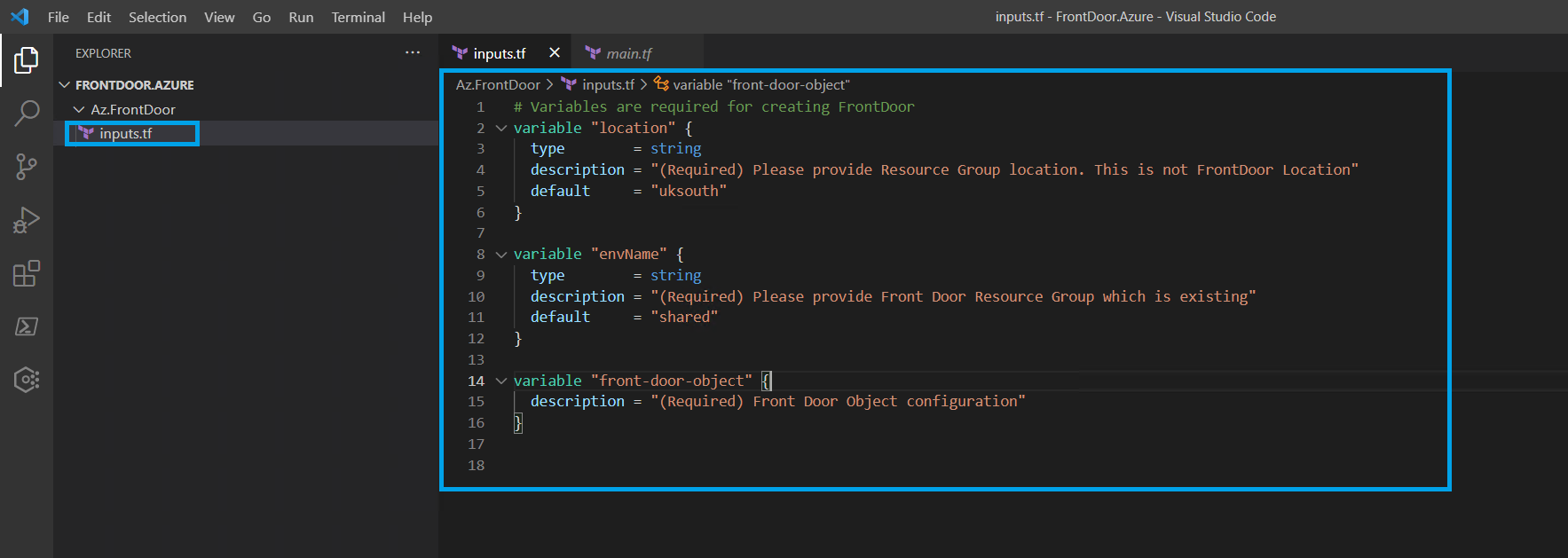
After completing the pre-requisites, we can now take further steps. Firstly, we will create a file named inputs.tf in a project and plug the necessary information in for FrontDoor Deployment.
Everything inside this file contains the variables we will use in terraform. Categorizing different components while improving with Terraform always provides a more tidy and cleaner development process.
# Variables are required for creating FrontDoor
variable "location" {
type = string
description = "(Required) Please provide Resource Group location. This is not FrontDoor Location"
default = "uksouth"
}
variable "envName" {
type = string
description = "(Required) Please provide Front Door Resource Group which is existing"
default = "shared"
}
variable "front-door-object" {
default = {}
description = "(Required) Front Door Object configuration"
}
We can see two different variables in inputs.tf file, but it is actually three in sum. These variables are only stored in this file. Except for one of them, we can assume that these variables are not that complex to deal with. Front-Door-Object should be regarded as the most critical variable and object type. All information passed in this variable should be in a particular structure.
We will have a detailed example to show how the structure of a front-door-object should be in the following article. The file you see below is an example variable for the inputs.tf file. There are many different methods to pass the variables, but we can send these variables as inputs with the ".tfvars" file.
location = "uksouth"
envName = "shared"
##FrontDoor Variables
front-door-object = {
friendly_name = "fd-shared-myenv"
enforce_backend_pools_certificate_name_check = false
load_balancer_enabled = true
routing_rule = {
}
backend_pool_load_balancing = {
}
backend_pool_health_probe = {
}
backend_pool = {
}
frontend_endpoint = {
}
tags = {
}
}
We shared how an example tfvars file should be above for our terraform provisioning that we are developing. Now, let's create a file named main.tf and introduce the resources we want to deploy.
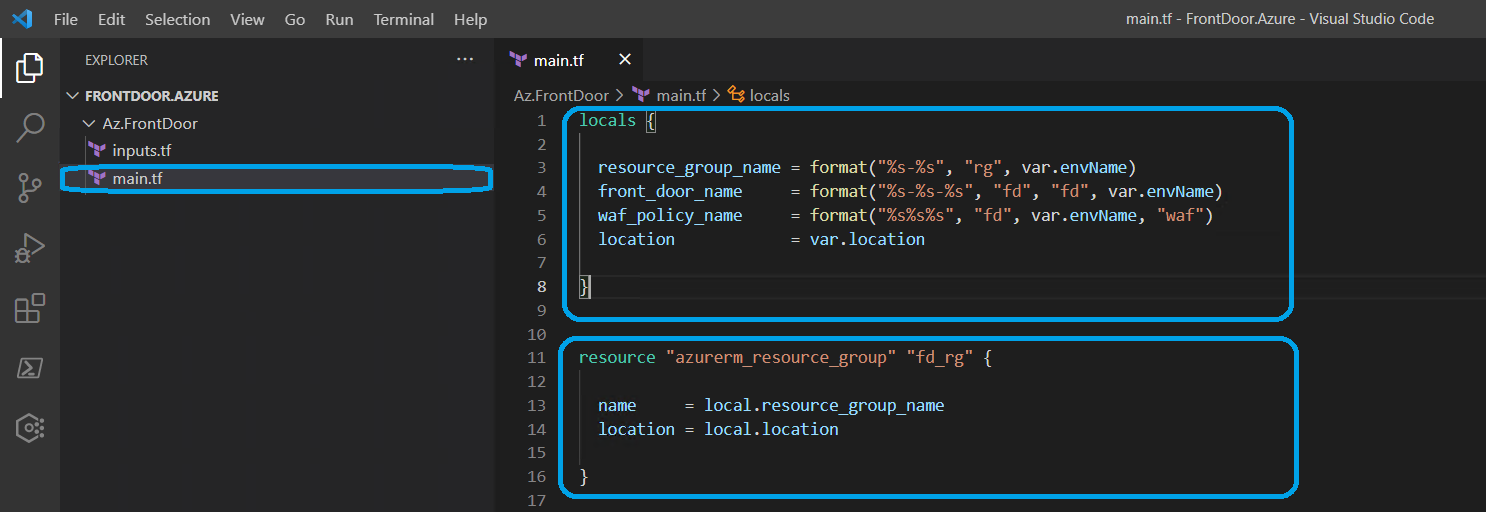
After creating main.tf file, we should define the locals and resource blocks in it. The definitions we will do are only about local and resource blocks in terraform. For now, we shall only use locals and azurerm_resource_group terraform blocks.
locals {
resource_group_name = format("%s-%s", "rg", var.envName)
front_door_name = format("%s-%s-%s", "fd", "fd", var.envName)
waf_policy_name = format("%s%s%s", "fd", var.envName, "waf")
location = var.location
}
resource "azurerm_resource_group" "fd_rg" {
name = local.resource_group_name
location = local.location
}
As you can see, we made some definitions above. And now, let's use terraform init and terraform plan commands. The result must be similar to the image below. To successfully execute the terraform plan command, we need to define our environment variables first.
$env:ARM_CLIENT_ID = "d03e4b85-XXXX-XXXX-XXXX-5d2dc9313749"
$env:ARM_SUBSCRIPTION_ID = "a25a223b-XXXX-XXXX-XXXX-4fda84986cd5"
$env:ARM_TENANT_ID = "2596de33-XXXX-XXXX-XXXX-069cfce79321"
$env:ARM_CLIENT_SECRET = "---secret-value-here"
To connect these variables to an Azure Subscription, we need to define them first. After completing this part, we can now use the terraform init command.
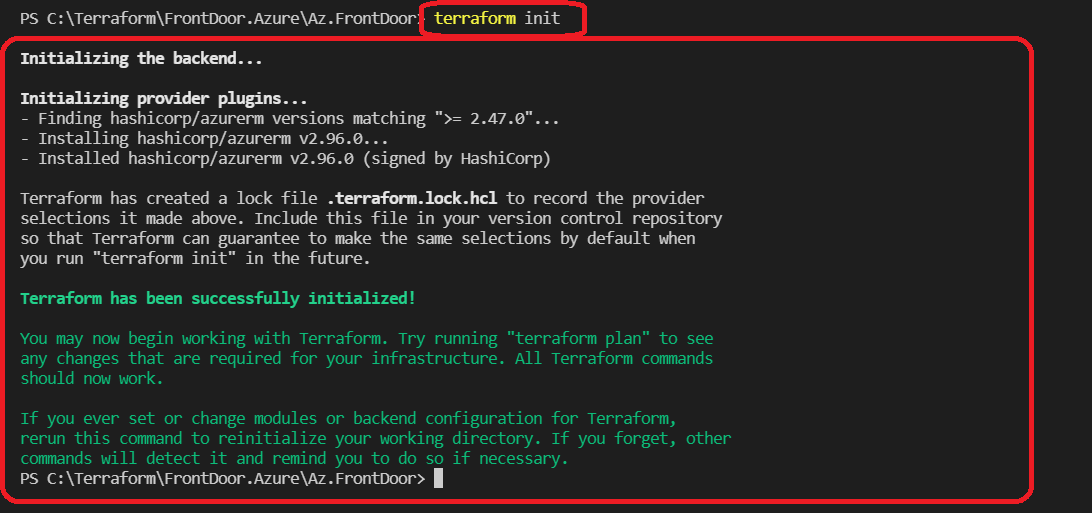
By executing the terraform init command successfully, we run the terraform plan command and get a result like below.
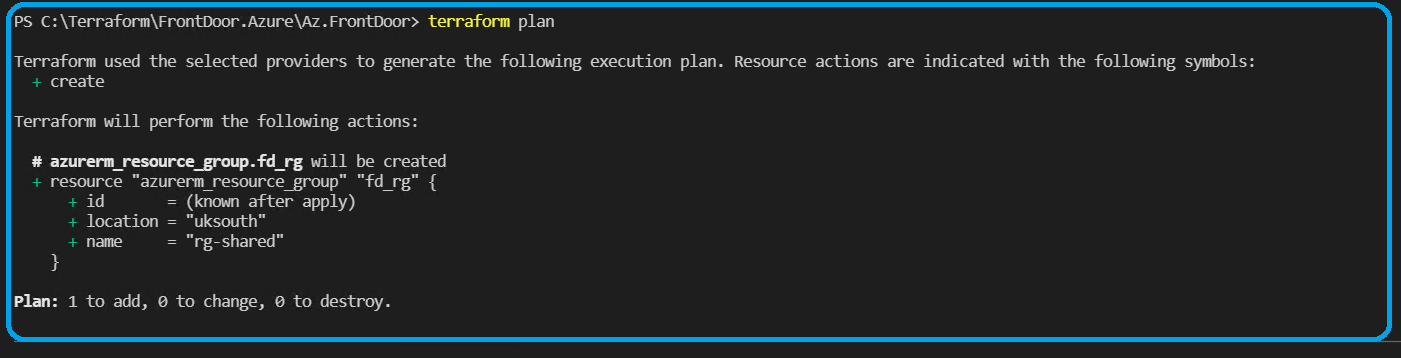
An important thing to notice is that we did not use any back-end for the terraform state in this demo. We can use Azure Blob Storage, S3, or Terraform Enterprise as an instance in our following articles.
In the next article, we will define the Azure FrontDoor resource block that we target.