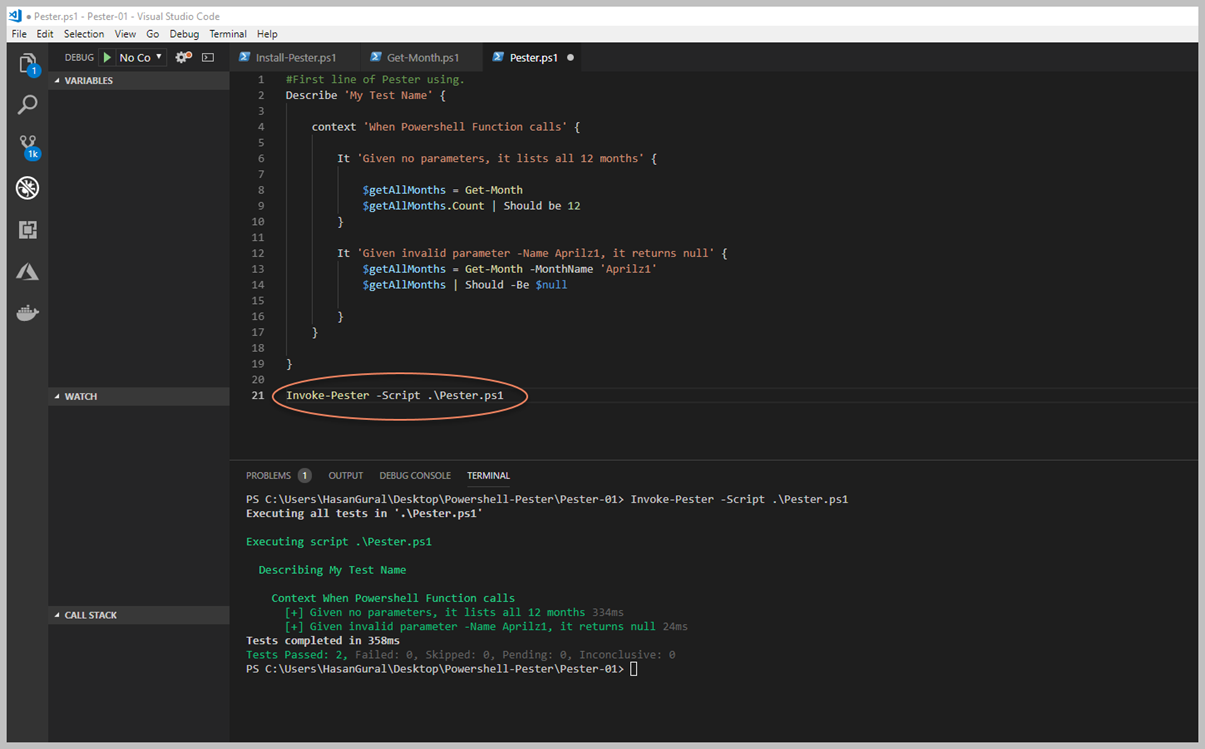
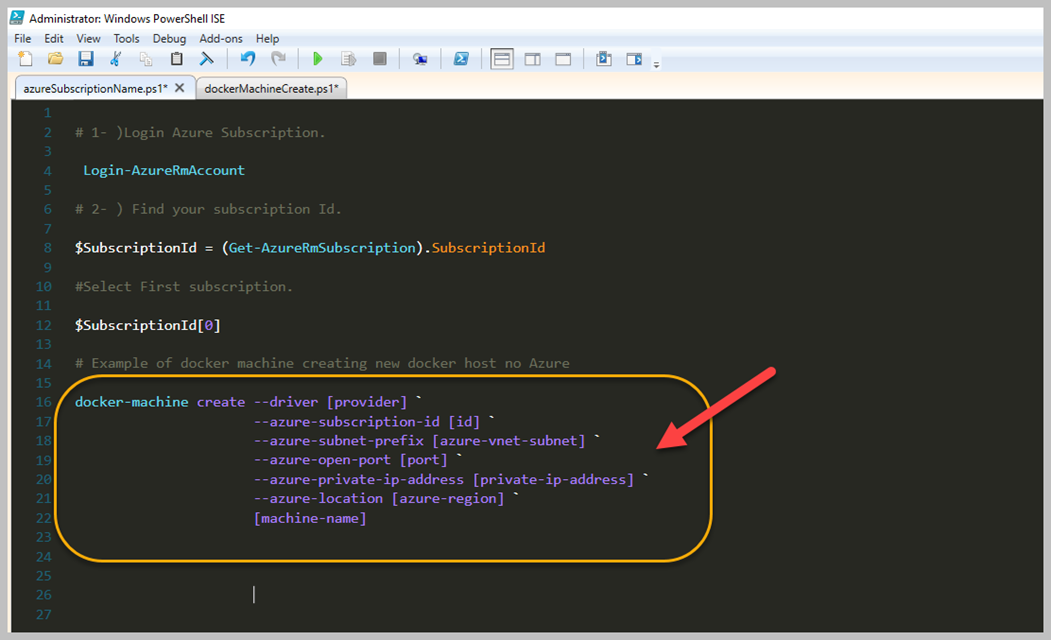
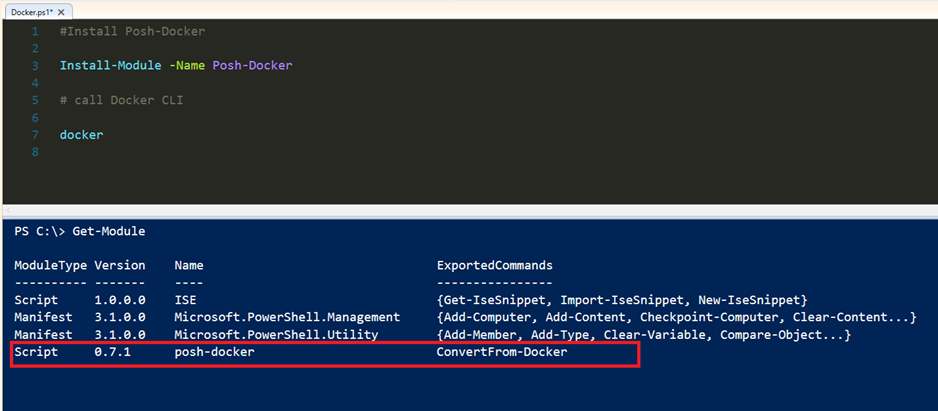
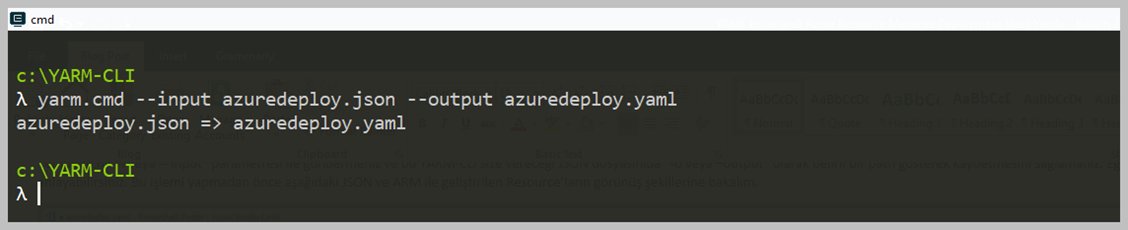
Packer serimize Provisioners' ile devam ediyoruz. Packer Image Template'leri içerisinde, 'Provisioners' bölümü en çok dikkat çeken kısım olarak karşımıza çıktığını daha önce belirtmiştim. Packer ile oluşturmak istediğiniz imaj için öncesinde içerisinde olmasını istediğiniz yazılımı yüklemek veya işletim sistemini yapılandırmak için kullanması gereken bir özelliktir. Basit olarak bunu kullanmanızda birçok aşama var. Öncelikle bildiğiniz gibi bir imaj alırken, Sysprep önem arz eder, bunun dışında belki o imaj içerisinde belirli bir yazılım olsun, Registry içerisinde şu şekilde bir kayıt olsun, bunu değeri bu olsun, hatta Package Management üzerinden bir yazılım yüklensin gibi her türlü detayı belirtebiliryorsunuz. Öncelikle 'Provisioners' isteğe bağlıdır. Bir şablon içinde hiçbir hazırlayıcı tanımlanmamışsa, sonuçta ortaya çıkan makine görüntülerine varsayılanlardan başka hiçbir yazılım yüklenmeyecektir. Bununla birlikte, bu tipik değildir, çünkü Packer'ın değerinin çoğu önceden yapılandırılmış yazılımın çoklu özdeş resimlerini üretmektir. Provisioners genellikle bir Powershell Script, bash script vb. nitelikler ile tanımlanır.
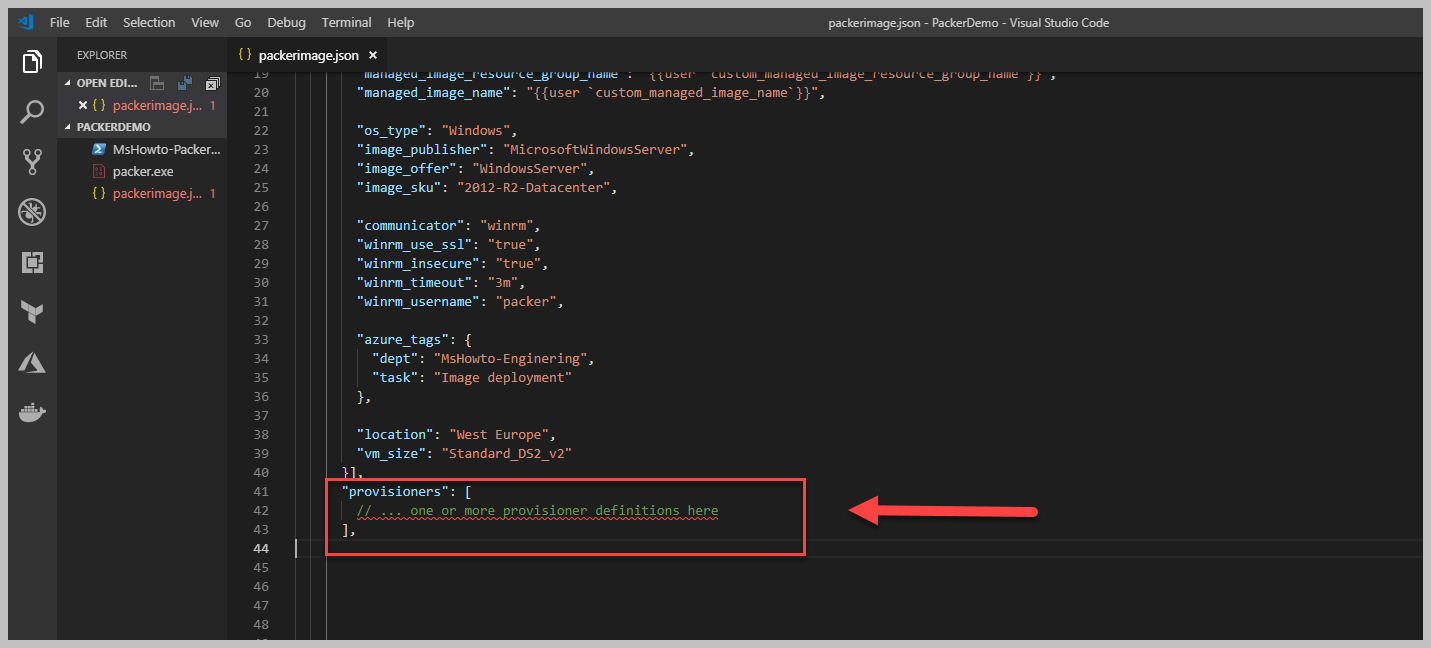
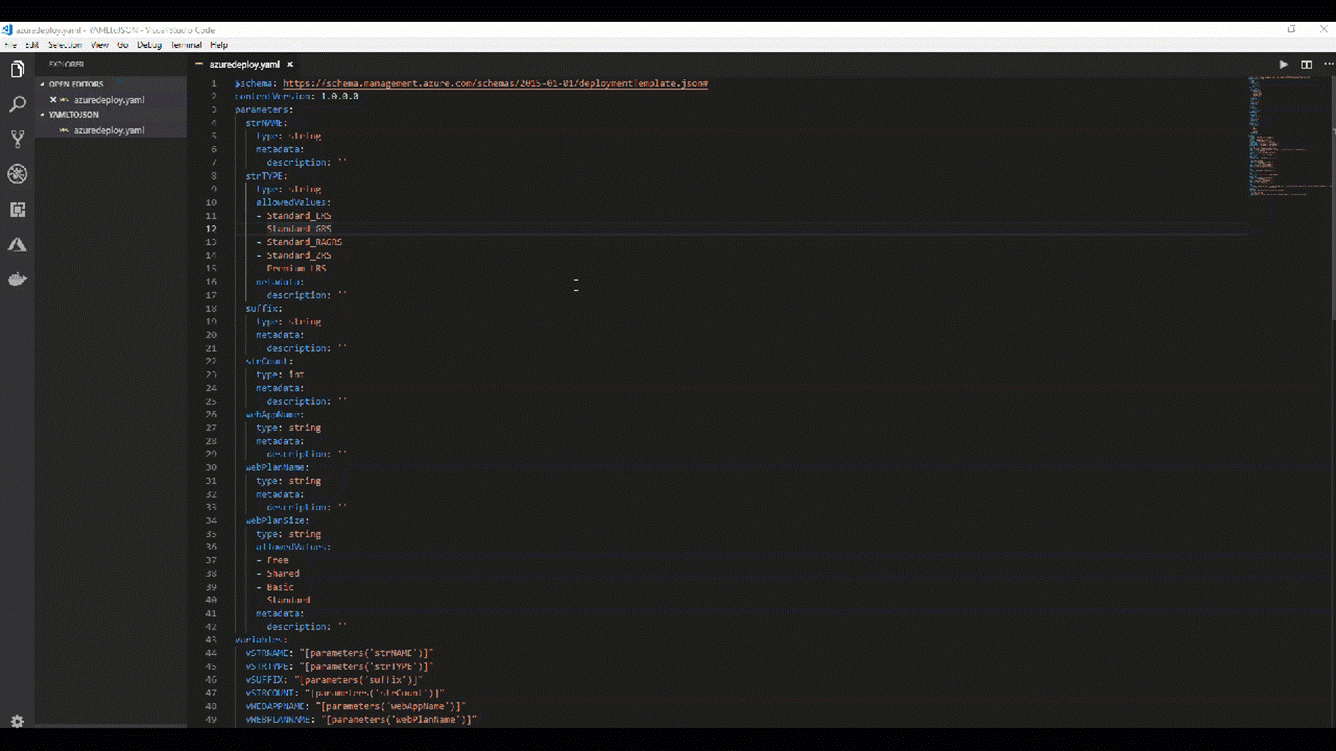
Yukarıda görüleceği gibi basit bir haliyle mevcut imaj için tanımladığımız JSON dosyamızın son bölümüne, 'Provisioners' adında yeni bir nitelik tanımladım ve artık bunun içerisinden Powershell, Shell gibi komut satırları aracılığı ile istediğimi yapabileceğim. İstediğim derken? Hayal gücünüze kalan bir detay burası, tamamıyla size ait, isterseniz, bir Web Server install edebilir, isterseniz Scale Set kullanıyorsanız, Scale Set sonrası image içerisinde yapılması gerekenleri script içerisinde yazarak hızlı bir şekilde image haline getirebilirsiniz. Şimdi ise basit bir Powershell Script tanımlaması yapalım ve neler olduğunu görelim.
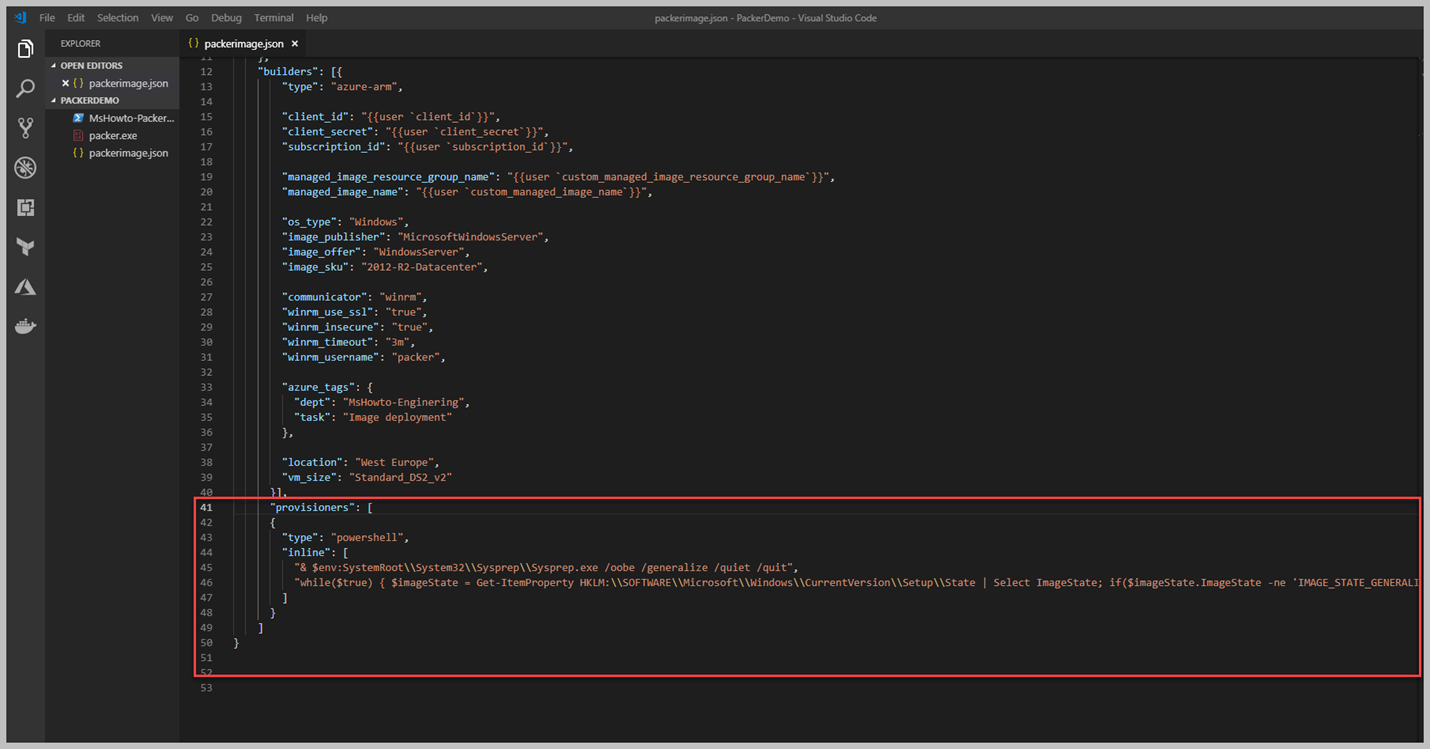
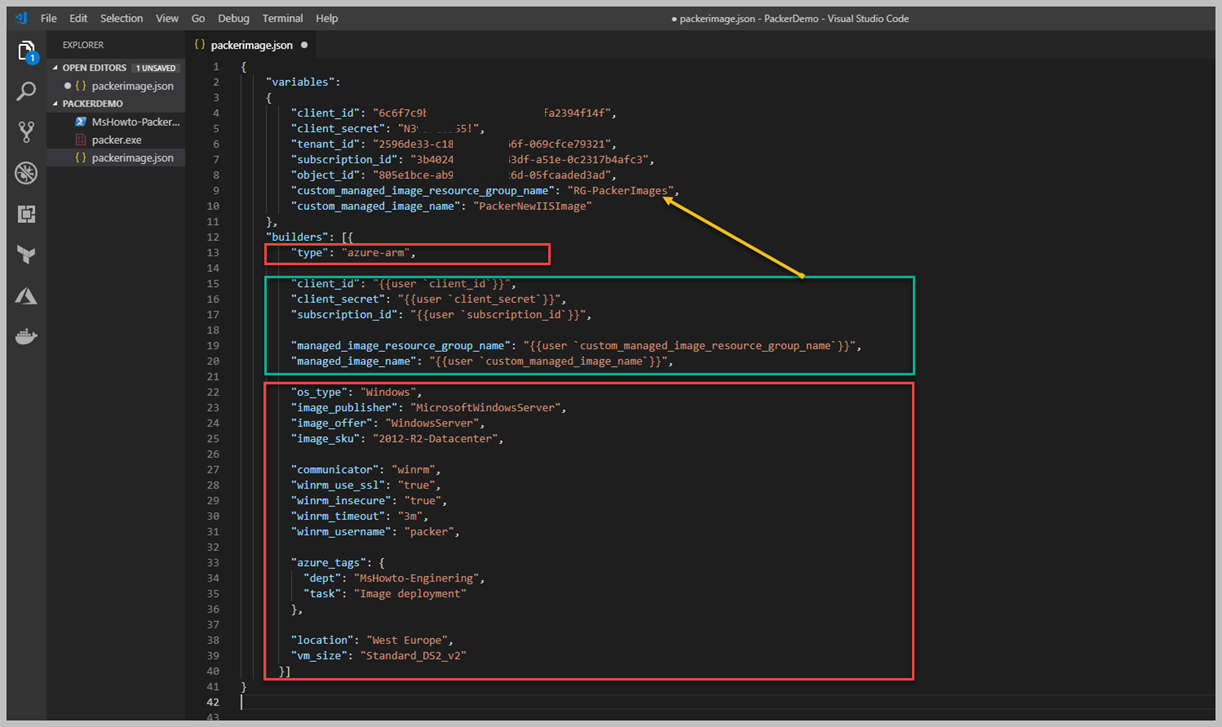
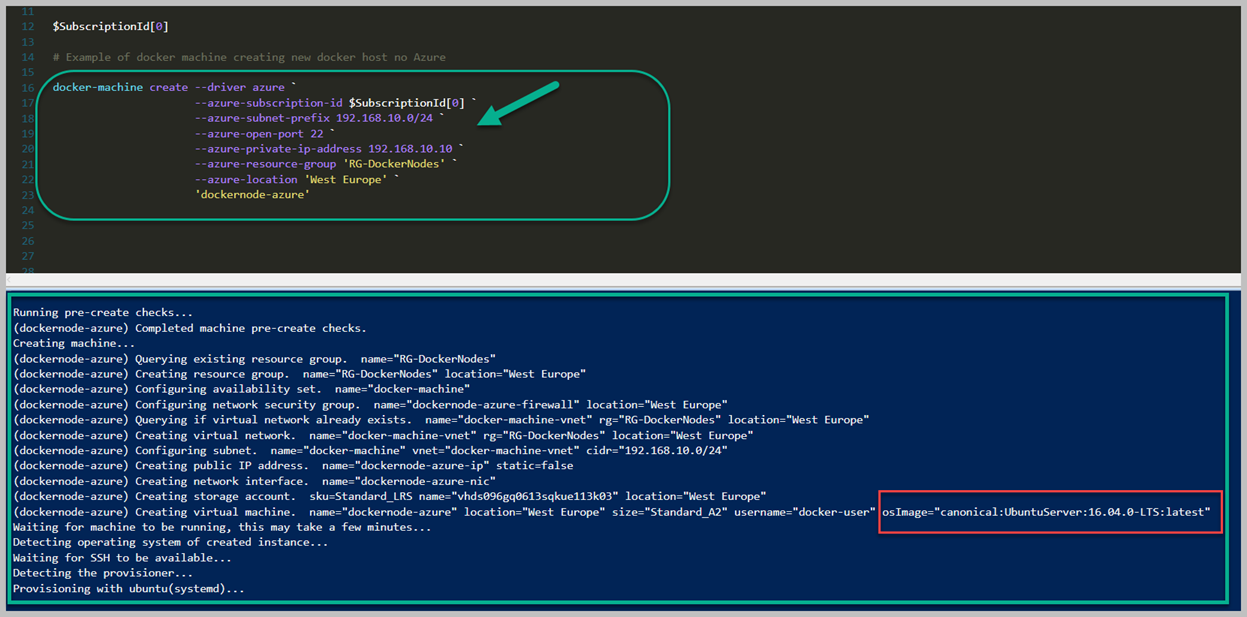
Kırmızı alan içerisine aldığım satırlarda örnek olması için Provisioners bölümünü ekledim ve 'type' olarak Powershell yazdım. Tekrar söylemek gerekirse, Provisioners olmadan bir imaj yaratmanız neredeyse imkansız, biz Builders içerisinde Microsoft kütüphanesi içerisinden hazır bir imajdan faydalandık. Fakat bizim için sadece clean bir Windows Server vermekte, fakat biz bunun üzerine bir ihtiyacımız olan kısmı ekleyerek imajımızı kurumumuza göre geliştirebiliriz. Şimdi sizinle bir Powershell Script dosyası oluşturup içerisine birkaç satır yazacağız. Bunun amacı tamamen image içerisine yapılması gerekenleri belirtmek. Örneğin bu image'ın adını WebServerIIS olarka vermiş idik ve anlamlı hale gelmesi için Windows Server içerisindeki IIS ve birkaç daha features ekleyecek script geliştirelim.
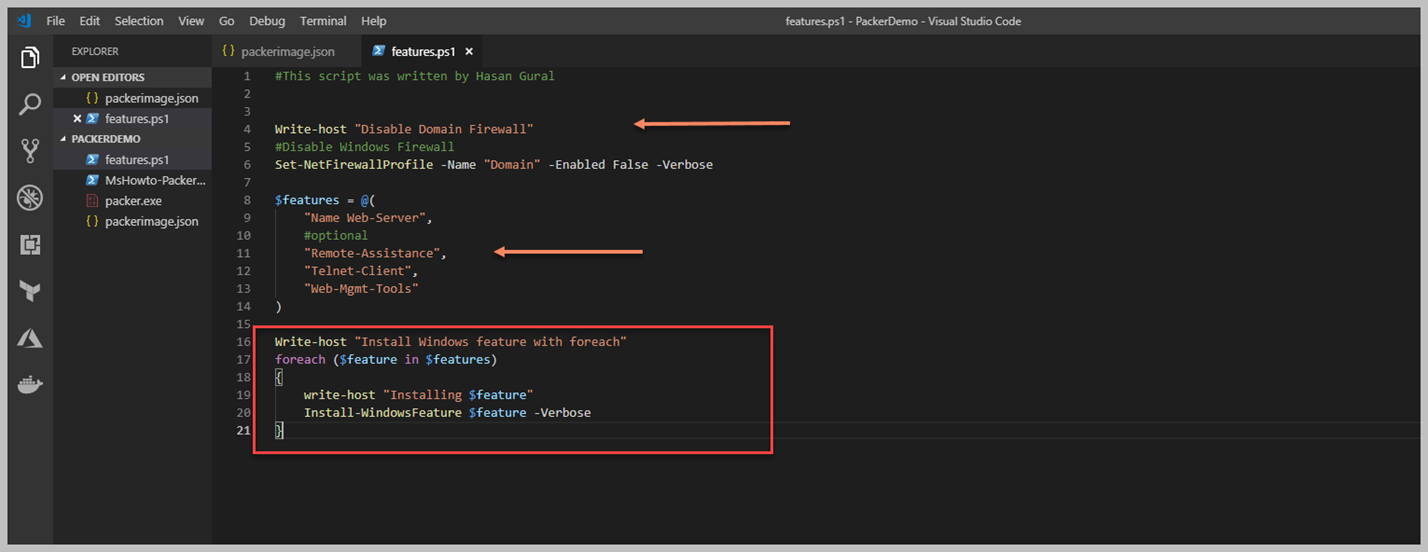
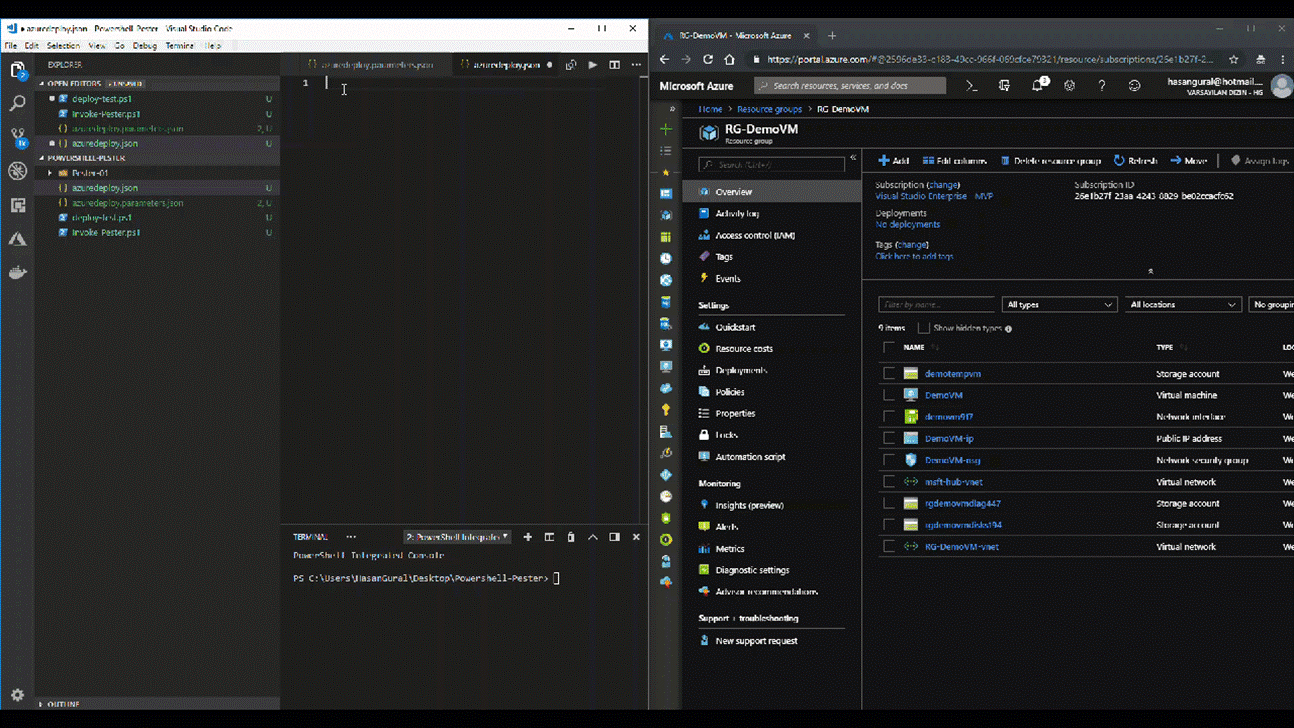
Features.ps1 isimli bir script geliştirdik. Şimdi bu Script içerisinde Windows firewall kapatmak için bir cmdlet yazdık ve bununla beraber Windows Server Feature aracılığı ile" Web-Server, Telnet-Client" vd role ve features kurulumunu yapması için gerekli Powershell Script yazdık. Peki şimdi bunu mevcut image template içerisine nasıl koyacağız. Bir önceki resim içerisinde bir Powershell satırlarını direk template içerisine yazmıştık. Şimdi ise bizim Powershell Scriptimizi ekleyeceğiz. Bunun için hemen template içerisine belirleyelim.
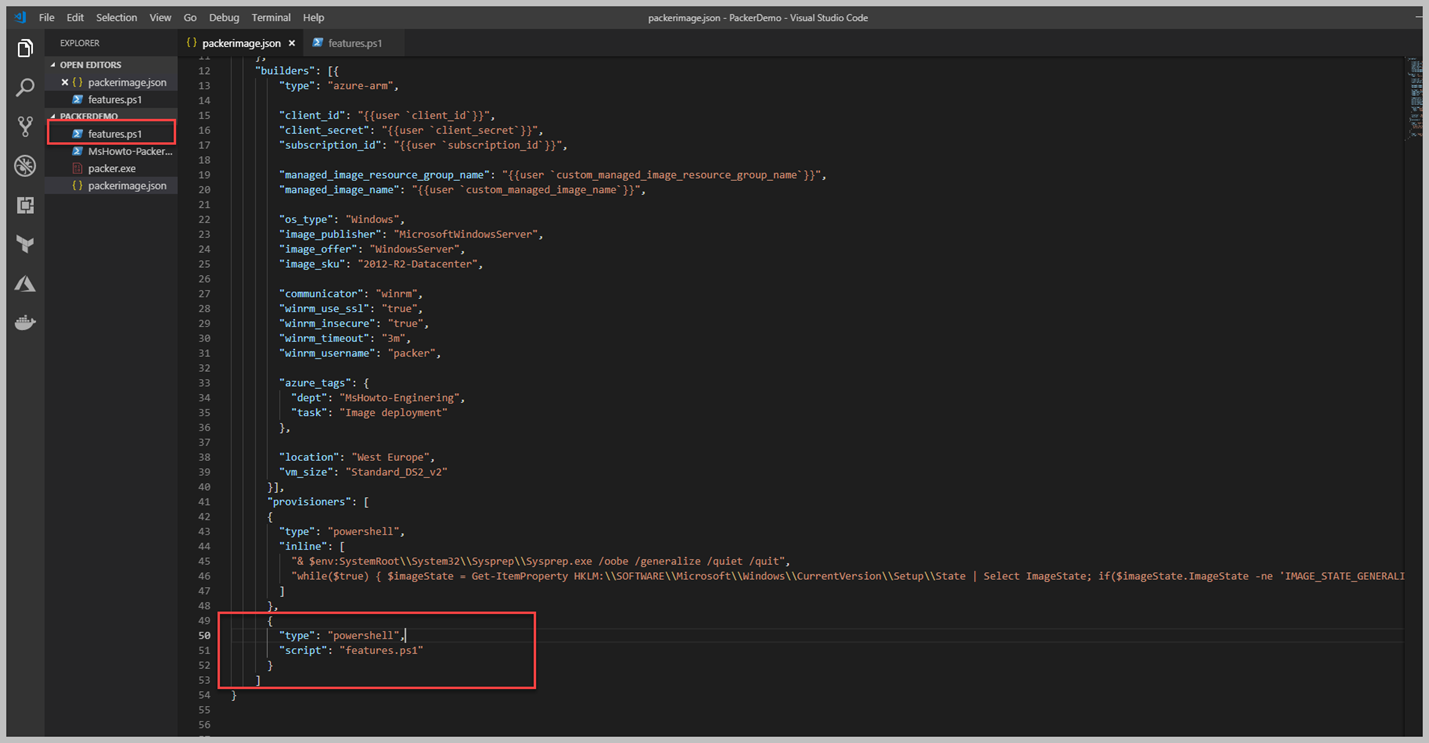
Yukarıdaki resim içerisinde görüleceği üzere, yeni bir satır ekleyerek Powershell ve mevcut scriptimizi tanımlamasını yaptık. Sizinle beraber yazmaya başladığımız bu Image dosyası ( JSON) oldukça karmaşık ve istediğimiz seviyelere geldi. Bir sonraki yazımızda packer aracının kullanım şeklini ve nasıl çalıştığına değiniyor olacağız.